This article reviews 24 major privacy projects that utilize zero-knowledge-proof technology.
Written by: Angelilu, Foresight News.
This week, the Ethereum DevConnect was held in Istanbul, Turkey. Among the hundreds of side events, those related to ‘zk’ accounted for as much as one-fifth, highlighting the developers’ significant interest in the ‘zk’ field.
In the encrypted world, there seems to be an unwritten rule that projects starting with “zk-” usually have a strong technical background. The “zk” mentioned here refers to Zero-Knowledge Proof (ZKP). The ZKP technology was first proposed in the field of cryptography in the 1980s, but it remained relatively obscure due to a lack of practical applications. Only in recent years, with the introduction of blockchain technology, has it come to the forefront again. Currently, apart from blockchain, it has also been widely used in fields such as cloud computing and machine learning.
What exactly is a Zero-Knowledge Proof? Michael Blau, a partner at a16z, even referred to ZKP as a great magic in a recent article. To better understand this concept, let’s compare traditional verification with zero-knowledge proof.
Firstly, both traditional verification and zero-knowledge proof structurally involve two roles and one event. Among the two roles, one is called the prover and the other is the verifier. The task of the prover is to prove the authenticity of an event to the verifier.
- Traditional verification: The prover must provide concrete evidence and undergo a rigorous verification process to ensure the event is true. Alternatively, the prover can use a proof by contradiction, providing evidence that the event could not be false.
- Zero-Knowledge Proof: The prover and verifier can exchange some information not directly related to the event. Then, the verifier can determine that the event is true, but only to the extent that he can ascertain it himself. Even if a third-party observer closely tracks the entire process, they can not draw the verifier’s conclusion.
Applications of Zero-Knowledge Proofs in the Blockchain Field
Within the realm of blockchain, the characteristics of ZKP (Zero-Knowledge Proofs) endow it with significant value when tackling two primary issues: privacy and scalability. In terms of scalability, zk-Rollup technology, based on ZKP, has always been a strategy favored by Vitalik. Projects like StareWare, zkSync, and Scroll leverage zero-knowledge proofs to enhance Ethereum’s scalability capacity.
Compared to other areas, zero-knowledge proofs have received relatively less attention when it comes to addressing privacy, even though privacy remains one of the most sensitive and widely-discussed topics in the blockchain technology space. While blockchains inherently offer a level of anonymity, their open ledger structure means any transaction can be viewed by anyone. When transaction addresses are linked to specific entities, an analysis of those transactions could potentially expose that entity’s private details. Thus, there’s still a need for enhanced privacy in many niche areas.
Zero-knowledge proof technology plays a pivotal role here. By employing this technology, both parties involved in a transaction can validate it without revealing any additional information, safeguarding user privacy and also reducing the risk of fraud and illicit activities to some extent. Currently, the demand for privacy applications in blockchain hasn’t been fully explored, and niche sectors aren’t getting the attention they deserve. This article will primarily focus on the application and impact of zero-knowledge proof technology concerning privacy.
The following sections lists 24 key privacy projects that utilize zero-knowledge proof technology, categorized into Layer 1 Public Chains, Layer 2, Developer Tools, and Applications.

Privacy-centric Public Chains
Privacy-centric public chains can be understood as a fusion of public chains with added privacy features. Three primary technologies used to enhance privacy in these chains include Zero-Knowledge Proofs (ZKP), Secure Multi-Party Computation (MPC), and Trusted Execution Environments (TEE). Oasis and Secret Network are currently among the more mature projects in this arena. However, it’s worth noting that neither of these projects directly employ ZKP technology. Given the intricate nature of ZKP, its research and development have been relatively slow, with real-world applications still being rare. This situation suggests immense untapped potential in this sector, yet a clear market leader is still to emerge.
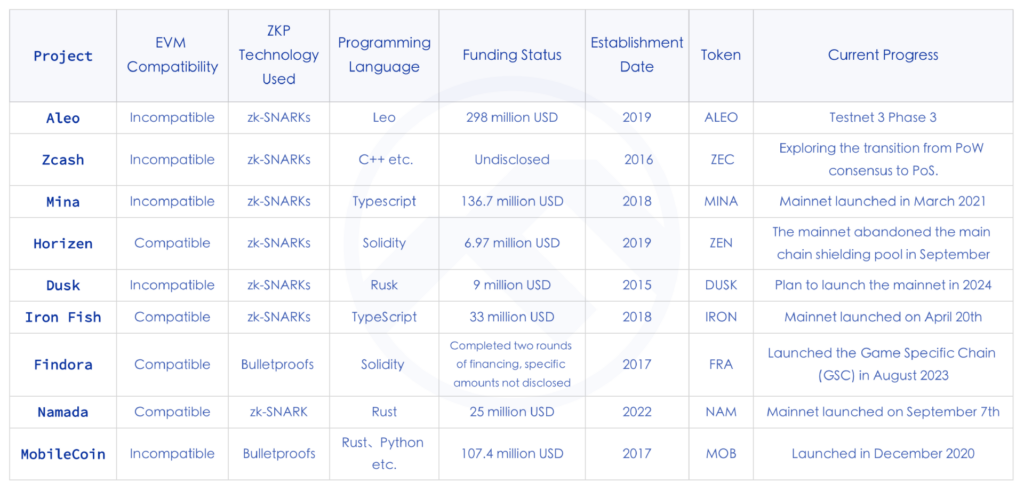
Aleo
https://www.aleo.org/
Aleo is a blockchain that utilizes zero-knowledge proofs for privacy and programmability. It has built a private-by-default, open-source blockchain to address the lack of privacy protection inherent in many blockchains. The Zexe framework is its zero-knowledge solution, allowing offline computations followed by online transactions that can prove their correctness without revealing transaction details. This ensures rapid verification by anyone. As a public chain, Aleo boasts its own virtual machine snarkVM, programming language Leo, development environment Aleo Studio, and the PoSW consensus algorithm. With its advances in the realm of zero-knowledge proofs, it has substantial market potential.
Founded in 2019, Aleo has raised almost $300 million in funding. Although it has yet to launch its mainnet, with previous plans for a July 2023 launch apparently postponed. The incentive deployment for its third testnet recently concluded on August 21, suggesting that the mainnet launch might take some more time.
Zcash
https://z.cash/
Zcash was one of the earliest “privacy coins”, pioneering the idea of using zk-SNARKs to enable shielded transactions and provide enhanced privacy beyond regular anonymous transactions. Focused on decentralized payments with privacy and anonymity, it uses zk-SNARK zero-knowledge proofs to authenticate off-chain data while concealing on-chain data, enabling users to make transactions that hide the amount, sender, and receiver. Zcash introduced creative uses of ZKP in the privacy coin sector, providing transparent addresses (t-addresses) that can be monitored on-chain and fully encrypted, untraceable shielded addresses (z-addresses).
Mina
https://minaprotocol.com/
Mina claims to be the world’s lightest blockchain, designed to remain consistently small in size despite increased usage. Using ZKP, it compresses the blockchain state to a mere ~22 KB. Mina employs succinct non-interactive zk-SNARKs to enhance Web3 accessibility and privacy. Its smart contracts, called zkApps, use encryption to protect user privacy, allowing users to interact by proving the authenticity of their data without actually sharing it. This not only increases user security and privacy but also reduces the responsibility of developers to safeguard sensitive data. Additionally, its zkApps utilize the widely recognized programming language, TypeScript, for smart contracts, making development more accessible. However, the ecosystem is not thriving, possibly due to the complexity of zk and its incompatibility with EVM.
Mina recently announced a significant mainnet upgrade introducing ZK smart contracts, allowing developers to more easily program zkApps using o1js. Preparations for the upgrade are underway, with testing segmented into four phases, of which the first two have already been completed.
Horizen
https://www.horizen.io/en
Horizen is a blockchain platform backed by zero-knowledge proof, equipped with zk-SNARKs, allowing for selective privacy. This lets users have optional anonymity. Horizen is EVM-compatible with the Ethereum Virtual Machine, dubbed Horizen EON.
A significant feature of Horizen is its architecture, which consists of a main chain and side chains. These chains communicate via a Cross-Chain Transfer Protocol (CCTP) for ZEN coin transfers. Due to regulatory pressures, from April this year, Horizen announced the removal of privacy from the main chain and ZEN. It is expected that by September, they will discontinue the main chain’s shielded pool and cease support for shielded transactions from transparent addresses (T-address -> Z-address) at the main chain level. However, privacy isn’t entirely abandoned; side chains will be dedicated to scalable data privacy.
The changes in Horizen highlight how privacy-focused blockchains are navigating tough regulatory environments. It also underscores the impact of the regulatory environment on privacy, with incidents like the arrest of Tornado Cash’s founder sounding alarm bells for major privacy protocols.
Dusk
https://dusk.network/
Dusk is a Layer 1 blockchain protocol with privacy protection features, specially designed for business compliance. Its network security is ensured by a novel Proof of Stake (PoS) consensus mechanism named Succinct Attestation, which also meets critical financial requirements for settlement consistency.
Dusk stands out for its blend of privacy and compliance. It offers a KYC solution that ensures customer privacy, based on the PLONK ZK algorithm.
Iron Fish
https://ironfish.network/
Iron Fish is a decentralized, Proof of Work (PoW) based, censorship-resistant, and publicly accessible blockchain project. Inspired by the zk-SNARK based Sapling protocol, it aims to ensure privacy for every transaction. Unlike other optional privacy blockchains, Iron Fish hides transaction details, mining info, wallet data, and more, making it only visible to the private key owner, ensuring absolute privacy.
Manta Network
https://manta.network/
Manta is the first privacy-focused network in the Polkadot ecosystem that relies on zk-SNARK. It has its unique UTXO-based wallet address system. Users can store, transfer, and exchange private assets. Primary Manta products include MantaPay, the privacy-centric zkSBT, and the Manta Wallet.
Findora
https://findora.org/
Findora is a privacy-protecting blockchain based on zero-knowledge proofs, boasting programmability. Developers can create privacy-centric applications (zkDapps) on it and deploy modular subnets customized for specific dApp needs, letting users control data visibility on the chain. Moreover, it’s EVM-compatible and, through its cross-chain transfer feature, can act as a second layer to enhance Ethereum’s privacy. Recently, Findora launched a Game Specific Chain (GSC), a new subnet providing a development environment for zero-knowledge Web3 games.
Namada
https://namada.net/
Namada is a Proof of Stake L1 designed for inter-chain asset oblivious privacy. It aims to shield transfers of any assets, fungible or non-fungible, owned by multi-chain users using zero-knowledge proof techniques. In May, its parent company, Anoma Foundation, announced a funding round of $25 million led by CMCC Global.
MobileCoin
https://mobilecoin.com/homepage
MobileCoin (MOB) is a cryptocurrency designed for everyday transactions with a mobile-first approach. Apart from the sender and the receiver, no one can see the transaction details. MobileCoin achieves privacy using zero-knowledge proof technology and employs a unique ZKP known as Bulletproofs to construct “range proofs” for encrypted values. Bulletproofs represent concise, non-interactive ZKPs.
Privacy Layer 2
In addition to building entirely new blockchains with integrated privacy features from the ground up, many projects have also opted to leverage zero-knowledge technologies to add a privacy protection layer to existing blockchains. This approach allows these existing blockchains to address scalability issues while also ensuring privacy. By combining zero-knowledge technology with blockchain to solve specific problems, these solutions offer greater composability compared to whole blockchains.
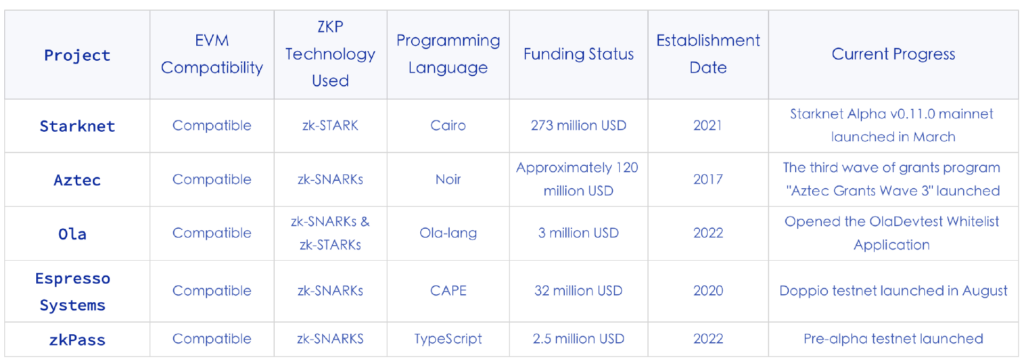
Starknet
https://www.starknet.io/en
Starknet is a decentralized ZK rollup based on Ethereum, launched by StarkWare. It aims to enhance the scalability and privacy of blockchains by leveraging zk-STARK proof technology.
Aztec
https://aztec.network/
Aztec offers a privacy and scalability solution based on ZK Rollup, featuring a two-layer zk-zkRollup design. One zk layer encrypts user transactions privately, while the other compresses these transactions. This allows Aztec to succinctly prove numerous encrypted state transitions without being EVM-compatible. In March, they announced the discontinuation of their privacy infrastructure, Aztec Connect, shifting their focus to developing the general-purpose zero-knowledge language Noir and its underlying blockchain. Their latest undertaking revolves around building privacy abstractions to provide developers with privacy for smart contracts, including default anonymity, private state read/write capabilities, and private smart contract function executions.
Ola
https://Olavm.org/
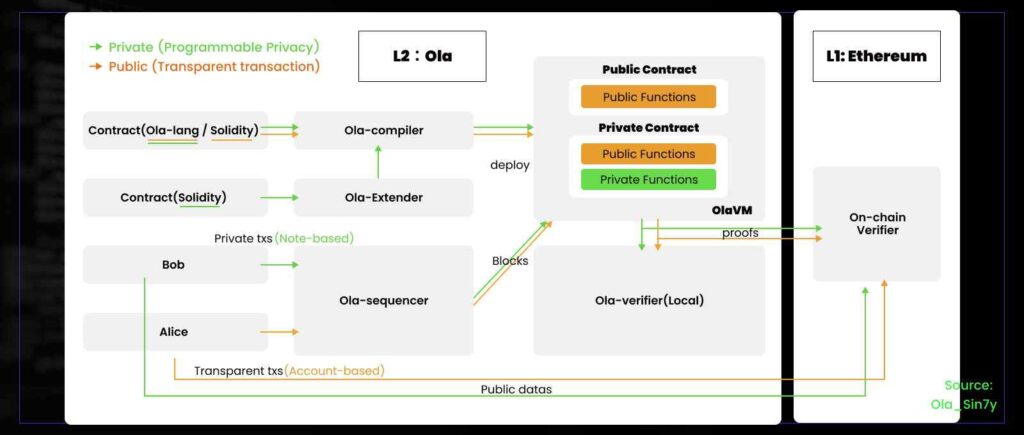
Ola is a ZK-ZKVM Rollup platform emphasizing scalable privacy, compliance-friendliness, programmable privacy, scalability, and multilingual compatibility. It aims to augment all programmable Layer 1 blockchains with privacy and scalability as a Layer 2 solution, featuring Turing completeness and storage access support.
Key products include the ZK-friendly virtual machine Ola-VM and the smart contract language Ola-lang. The latter is a general-purpose language based on ZK-VM, boasting high programmability, allowing for the deployment of any smart contract, be it public or private. Their ZK-friendly VM, Ola-VM, uses a Reduced Instruction Set Computer (RISC) architecture to achieve higher performance with full zk-friendly design and non-deterministic computation support. The code for Ola-lang smart contract language and OlaVM virtual machine is now open source to the developer community.
Ola completed a $3 million seed funding round in July this year. Recently, it has supported the Poseidon2 hash in its proof system, which, compared to the original Poseidon hash, has resulted in an over 40% performance improvement for the prover. Additionally, Ola announced during the Turkey DevConnect the opening of whitelist applications for the Ola DevTestnet, providing a channel for developers and general users to participate in Ola. Its public testnet and mainnet are scheduled to launch sequentially in 2024.
Espresso Systems
https://www.espressosys.com/
Espresso Systems acts as a decentralized sequencer and data availability system, connecting various Layer 2 scalability solutions and supporting both Optimistic and ZK Rollups. Regarding privacy, they’ve developed and open-sourced a configurable asset privacy smart contract named CAPE using zero-knowledge proof technologies. This enables digital asset creators to determine who can view custody and transfer data related to their created assets. Users can create new tokens or wrap existing Ethereum tokens to bestow desired privacy attributes.
zkPass
https://zkpass.org/home
zkPass is a privacy-preserving protocol designed for private data verification. Built on Multi-Party Computation (MPC), Zero-Knowledge Proofs (ZKP), and Tripartite Transfer Layer Security (3P-TLS) technologies, zkPass offers TransGate, enabling users to selectively and privately verify their data on HTTPS websites within the Web3 realm. It can encompass various data types, such as legitimate identities, financial records, healthcare information, social interactions, work experiences, education, and skill certifications, among others. Incubated by Binance Labs, zkPass recently secured $2.5 million in funding this August.
Developer Tool
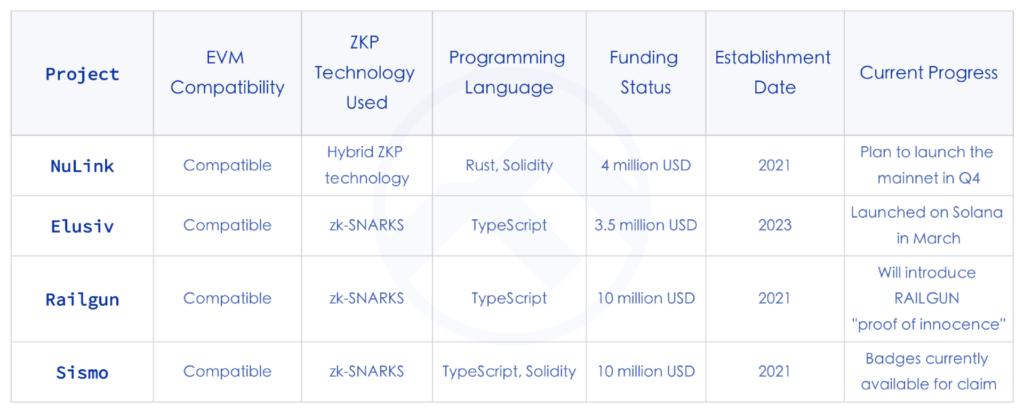
NuLink
https://www.nulink.org/
NuLink is dedicated to offering out-of-the-box privacy solutions. Through its API, developers of decentralized applications can easily implement privacy in their projects. The architecture of the NuLink network encompasses application, cryptographic, storage, blockchain layers, and an observer network. By 2024, it’s anticipated to roll out a data availability mechanism that supports ZKP and privacy data computation backed by Fully Homomorphic Encryption (FHE).
Railgun
https://www.railgun.org/
Built on the Ethereum platform, Railgun is a privacy and anonymity solution capable of directly interfacing with DEXs, lending platforms, and smart contract applications. Leveraging Zero-Knowledge Proofs, Railgun ensures privacy protection over a user’s financial status, personal identity, and behavioral patterns. It also offers selective transparency, granting users the choice to reveal specific identity or financial details when necessary, such as during audits or regulatory requirements.
A standout feature of the system is its three core functionalities: Add, Split, and Remove. Each operation, built on zero-knowledge proofs, offers varying degrees of privacy and anonymity. Users can select these operations based on their needs and even combine multiple operations into one transaction to reduce Ethereum network gas fees.
Sismo
https://www.sismo.io/
Employing Zero-Knowledge Proofs (ZKP) and privacy-preserving technologies, Sismo allows users to aggregate their identities and selectively disclose personal data to applications. Sismo Connect serves as a developer-friendly layer atop the proof scheme. Through requesting and validating ZK proofs, developers can access personal data without compromising user privacy. Distinctively, compared to other protocols emphasizing data privacy, Sismo places a greater emphasis on identity privacy.
Privacy application
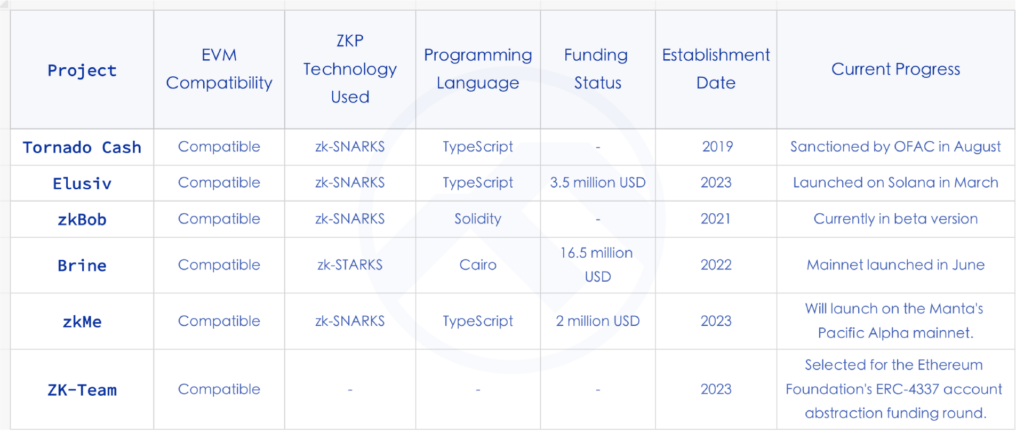
Tornado Cash
https://ipfs.io/ipns/tornadocash.eth/
Tornado Cash is a privacy transaction tool that employs Zero-Knowledge Proofs (ZKP), specifically zk-SNARKs, to anonymize transactions, operating essentially as a mixer. Due to its privacy features, it has been linked with hacking incidents and money laundering. A report last year indicated that nearly 75% of the money laundering on the Ethereu
m network was facilitated through Tornado Cash. The platform recently faced regulatory challenges when the U.S. Department of Justice arrested co-founder Roman Storm on August 24. Both Roman Storm and another co-founder, Roman Semenov, face charges of conspiracy to launder money, sanctions violations, and operating an unlicensed money transmission business.
Elusiv
https://www.elusiv.io/
Elusiv is a compliance privacy protocol based on Zero-Knowledge, currently built on Solana. It utilizes zk-SNARKs to enable private transactions while emphasizing decentralized compliance, allowing users to decide which transactions to make public through Elusiv. Elusiv was launched on Solana in March this year and has since introduced privacy token trading features on Solana.
zkBob
https://zkbob.com/
zkBob offers a privacy solution based on stablecoins, deployed on Polygon and Optimism. It employs Zero-Knowledge Proofs to anonymize the sender, recipient, and amount during funds transfers. zkBob is compatible with over 15 EVM networks, and its token, BOB, is a multi-chain and multi-collateral stablecoin with optional privacy features.
Brine
Brine is an order-book privacy DEX, leveraging StarkWare’s zk-STARK proof technology for private transactions. It adopts a dual on-chain and off-chain component design, with Zero-Knowledge Proofs utilized for privacy and for transmitting off-chain transaction validity proofs to the chain. Brine launched its mainnet in June this year, boasting a total trade volume of approximately $500 million. In September, it secured $16.5 million in funding at a $100 million valuation, led by Pantera Capital, with participation from StarkWare, Spartan Group, and others.
zkMe
zkMe is a decentralized Web3 credentials network that uses Zero-Knowledge Proofs for secure and private credential issuance and verification. It focuses on end-to-end zero-knowledge handling and selective information disclosure. When users (credential holders) create a DID with zkMe, they receive a unique SBT, cryptographically bound to their public key, serving as identity proof. This enables users to validate their identity without revealing any sensitive information, thanks to ZKP.
ZK-Team
ZK-Team is one of the 18 projects selected in the recent funding round for the Ethereum Foundation’s ERC-43337 account abstraction. Introduced by the Canadian blockchain firm PriFi Labs, ZK-Team is a proof of concept for a privacy-protected abstract account that allows organizations to manage team members while maintaining their individual privacy. Through Zero-Knowledge Proofs, ZK-Team ensures transaction confidentiality concerning the different addresses and their associated quotas for team members.
Analysis of the Sector
Financing
From the analysis of the aforementioned projects, it’s evident that a16z invested in Aleo, Iron Fish, and Nym, while Sequoia Capital invested in Iron Fish, Espresso Systems, among others. The interest from top venture capital firms in ZK privacy projects due to market demand, technological innovation, and long-term value is apparent. The significant investments further underscore the potential and importance of this domain.
From a financing perspective, Aleo has so far received the highest funding among privacy blockchain projects, leading to high market expectations. However, due to repeated delays in the launch of its mainnet, there has been a gradual decline in attention towards the project. Recently, Aleo successfully advanced to the third phase of its testnet. Once its mainnet is successfully launched, it will mark a significant milestone in the privacy technology sector.
Establishment Timeline
The major privacy blockchains discussed were launched in 2018 and 2019. The reasons for this trend include the foundational blockchain and cryptographic technologies becoming more mature around this time, making Zero-Knowledge Proofs more adaptable in the blockchain domain. Additionally, from a regulatory standpoint, the General Data Protection Regulation (GDPR) of the European Union took effect in May 2018. Coupled with the implementation of other privacy regulations, both companies and individuals started emphasizing data privacy more, propelling the demand for privacy blockchains. Market dynamics also played a role; the blockchain and cryptocurrency markets witnessed a boom in 2017, leading to ample funds in the market. Compared to Ethereum and Bitcoin, privacy features became a distinct competitive advantage, directing some funds towards privacy blockchains.
However, the majority of infrastructures employing ZKP technology were established after 2021. This suggests that the market for privacy blockchains is becoming saturated, and the demand for privacy in conventional blockchains is becoming more pronounced. In recent years, there’s been a surge in ZKP infrastructures.
Choice of ZKP Technology
There are several implementations of Zero-Knowledge Proofs at present, including zk-SNARKs, zk-STARKs, PLONK, and Bulletproofs. Among the projects mentioned in this article, zk-SNARKs are the most commonly used. zk-SNARKs are employed to prove that a given computation has been executed correctly while keeping the inputs private. Its distinguishing feature is that its proof size is relatively small. On the other hand, zk-STARKs can operate without an initial trusted setup.
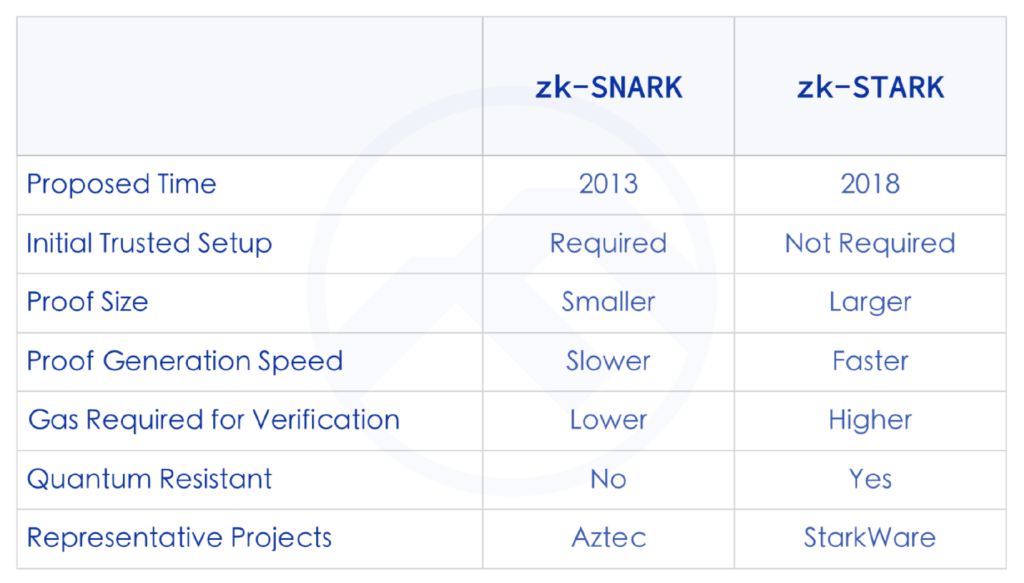
PLONK is a variant within the zk-SNARK proof systems. The trust setup for PLONK is universal, implying that it can be initiated once and then reused for all circuits. It’s also upgradable: new randomness can always be added until there’s confidence that the setup hasn’t been compromised. Bulletproofs, on the other hand, is a general zero-knowledge proof, mainly used for range proofs and typically employed within confidential transactions.
As illustrated above, different algorithms have their distinct technical features. As a result, many projects have adopted a hybrid approach to zero-knowledge proof algorithms in their implementation logic. Take the programmable privacy and scalability solution, Ola, for instance. It uses Starky as the proof-generation algorithm and selects Plonky2 as the recursive circuit algorithm. A commonality between the two is that they are both based on STARK, which means neither requires a third-party trust setup.
Smart Contracts and Programmability
Programmability refers to the feature in privacy projects that allows other developers or organizations to build upon and extend their privacy functions. Zero-knowledge proof technology, coupled with specially developed programming languages, assists developers in crafting privacy-centric applications. With the increasing demand for privacy, programmability in privacy projects is gaining more and more favor among developers and users. Projects like Aleo and Aztec, mentioned earlier, have this programmable characteristic.
Programmability comes in two forms: ZKDSL and ZKVM. ZKDSL allows developers to directly write low-level circuit constraints, making it easier to create circuits and zkDapps. For instance, Aztec’s programming language, Noir, and Aleo’s language, Leo, both adopt the ZKDSL format. However, the characteristics of ZKDSL mean it inherently has expressive limitations. The other form, ZKVM, is a better choice in terms of programmability. Protocols like Ola utilize ZKVM, and their smart contract language, Ola-lang, is built upon ZKVM.
Privacy Design
In the domain of blockchain privacy design, there are typically two primary data structure models: the UTXO (Unspent Transaction Output) model and the Account model.
UTXO: This is the model used by Bitcoin and some early blockchains. In the UTXO model, transactions don’t happen directly between accounts; instead, they’re realized by referencing unspent transaction outputs (UTXOs). Each new transaction creates a new UTXO while consuming old UTXOs. This model offers higher scalability and flexibility.
Account Model: Platforms like Ethereum that support smart contracts typically use the account model. In this model, each participant has one or multiple accounts, each with an associated state (like balance, contract data, etc.). Transactions occur directly between accounts, mirroring the operational style of traditional banking systems. Although this design is more intuitive and straightforward, it offers relatively limited possibilities in terms of privacy.
Most privacy protocols are designed using the UTXO model. Zcash’s UTXO-based Note structure can easily conceal the identities of transaction senders and receivers. Aztec, Railgun, Ola, and others also adopt the Note structure. However, there are nuances and slight variations among these projects, each with its strengths and weaknesses.
DApp Specific Privacy
Aztec’s privacy design relies on the UTXO (Unspent Transaction Output) model, which gives it excellent performance in terms of simple private transactions but limits the potential for developing complex smart contracts. Currently, the main application for Aztec is its in-house developed zk.money, a privacy payment platform based on zero-knowledge proofs. Although the platform performs admirably, the limitations of the UTXO model mean that if other projects want to integrate Aztec’s privacy features, they need to do so through a specially designed interface—the Aztec Connect gateway contract. This gateway contract acts as a bridge, allowing external projects to integrate with Aztec more easily, though doing so may introduce additional complexities and costs.
Programmable privacy
As previously discussed, the section on programmability highlighted a pertinent question: can the introduction of programmability within Aztec’s privacy technology address the challenges associated with developing intricate smart contracts? Using Ola as a case in point, its design wasn’t exclusively centered around a specific DApp privacy solution. Instead, it seamlessly integrated programmability. This empowers developers with the flexibility to deploy either public contracts (based on the Account model), private contracts (rooted in the Note model), or a hybrid of both (leveraging both Account & Note models). Such an approach not only caters to a myriad of privacy needs but also offers developers enhanced flexibility and room for creativity.
Compliance
One of the most pressing challenges facing privacy protocols today is the chilling effect of stringent regulations. In August 2022, the U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) imposed sanctions on Tornado Cash. Following the sanctions, the inflow of funds to Tornado Cash significantly decreased, plummeting by 68% within 30 days. In the same month, the U.S. Department of Justice arrested Roman Storm, a co-founder of Tornado Cash, charging him and another co-founder with conspiracy to launder money, violating sanctions, and operating an unlicensed money transmission business.
Due to their privacy features, privacy protocols have become essential tools for hackers. North Korean hackers have utilized protocols like Tornado Cash and Railgun for money laundering. Consequently, cryptocurrencies in the privacy sector have undergone several delisting episodes. The design for regulatory compliance in privacy protocols has become crucial. Recently, Vitalik Buterin proposed the concept of “privacy pools” in a paper, aiming to strike a balance between regulation and compliance of privacy protocols. This would allow users to publicly attest to potential sources of their withdrawals without compromising privacy.
Many projects now feature a “view key” function, allowing users to selectively disclose their transaction information. However, most protocols don’t enforce the view key feature, making it challenging to ensure users’ privacy levels. Additionally, these protocols often use an append-only private tree design, which lacks the necessary traceability for compliance purposes.
Notably, Ola incorporates an updatable Private Tree design and the view key function. Ola’s Private Tree is refreshable and supports tracing transaction paths, making privacy disclosures more automated and compliant. Through this design, users can manage their privacy more flexibly, share necessary information with regulators when needed, and still maintain a high level of privacy protection.
Summary
While zero-knowledge proof technology holds immense promise, it’s not without its shortcomings. Its implementation demands significant computational resources, which can potentially impact system efficiency. Consequently, a crucial challenge in current research and development lies in ensuring privacy without compromising system performance.
In the era of Web3, the significance of privacy is undeniable. The user’s demand for safeguarding sensitive information has rendered privacy-focused blockchains and applications indispensable in the Web3 landscape. These privacy chains offer robust programming languages and a comprehensive suite of development tools, drawing developers to actively engage and build upon them. However, one of the significant risks facing privacy infrastructure is the uncertainty surrounding the scale of its future demand. Furthermore, it’s plausible that various blockchains or projects might introduce native privacy protection features in the future, potentially posing a threat to third-party privacy-focused projects. Presently, projects like Aleo and Espresso Systems, which have garnered significant community attention, are still in their testnet phases, leaving their developmental trajectory uncertain. As a result, monitoring market trends and technological advancements remains paramount in the evolution of the privacy domain.



