1. Background
Blockchain, based on distributed consensus and economic incentives, provides a new solution for the establishment, storage, and transfer of value in an open, permissionless cyberspace. However, with the rapid development of the crypto ecosystem in recent years, crypto has increasingly been used for various risk activities, offering more covert and convenient methods of value transfer for online gambling, online activities in the black and grey industry, and money laundering.
At the same time, a group of web3 companies also use stablecoin like USDT as the main payment method in their business. However, these companies generally lack comprehensive risk control mechanisms such as AML, KYT, and KYC. This could lead to the possibility that USDT will flow unrestrictedly to business addresses, contaminating the funds of businesses and their customers.
This report aims to disclose the methods and scale of use of cryptocurrencies in risky crypto activities and track the flow of funds associated with risk activities through on-chain data, offering insights into the threat that risk cryptocurrencies pose to web3 companies.
2. Main cybercrime fields
The societal harm caused by online illegal criminal activities is increasingly severe. This harm includes direct damage to individual property and public safety, as well as indirect legal risks to individuals or corporate entities from industries associated with criminal activities. In recent years, countries have intensified their efforts to combat online criminal activities, making great progress in criminal legislation and research on the Internet ecosystem. However, cybercrime remains a challenging problem, especially with the emergence of new online spaces like blockchain. Traditional online gambling, activities in black and grey markets, and money laundering usually choose to use crypto or crypto infrastructure, thereby hindering legal identification and regulatory enforcement.
2.1 Online Gambling
Gambling which refers to betting money or material goods on an event with an uncertain outcome, primarily aims to win more money or material goods, meanwhile providing participants with psychological pleasure through the wager of funds or property. Online gambling involves gambling activities of different forms conducted over the internet, essentially replicating most of the major gambling methods found in real life.
In China, establishing gambling websites on computer networks for profit, or acting as an agent for those websites and accepting bets, falls under the category of “operating gambling houses” as stipulated in Article 303 of the Criminal Law. Citizens of the People’s Republic of China who gather to gamble or operate gambling houses outside the country’s territory, primarily targeting Chinese citizens as customers, can also be held criminally responsible under the law.
However, legal recognition of gambling and the operation of gambling houses vary in other countries or regions:
According to the Gambling Ordinance of Hong Kong, China, except for regulated horse racing, football betting, Mark Six Lottery, or other licensed gambling venues (like Mahjong parlors) and gambling activities exempted by law, all other gambling activities are illegal;
Under the Unlawful Internet Gambling Enforcement Act of the United States, it is illegal to conduct transactions with online gambling sites through financial institutions. However, State legislations vary, with differences in the legality and enforcement of online gambling activities;
According to the statement by the Gaming Inspection and Coordination Bureau of Macau, China, the Macau SAR government has never issued licenses for online gambling. Therefore, any information or betting websites promoting online gambling activities in the name of the Macau SAR government are fake and illegal. Public participation in these sites is not protected by Macau SAR law.
It is evident that online gambling is not illegal in all countries or regions. Licensed operations under local government supervision are not considered risk funds. Therefore, Bitrace’s report about online gambling activities is limited to unlicensed gambling platforms, agents of gambling platforms accepting bets beyond their licensed scope, and payment institutions providing financial settlement services to the former two.
Traditional online gambling platforms and their agents help gamblers settle funds through self-built centralized crypto deposit, transaction, and withdrawal systems, or by integrating crypto payment tools. Due to the anonymity of crypto, it is difficult for government departments to regulate or enforce laws against those activities. Nowadays new types of hash-based online gambling platforms are set up on blockchain networks, with betting, settlement of wagers, and accumulation and collection of funds that are all through smart contracts, making them more widespread and rapidly evolving.
2.2 Internet Activities in Black and Gray Market
The online black and grey market refers to the industrialized and chain-based industry formed in cyberspace with the aim of gaining illegitimate benefits through various technical means to implement or assist in criminal activities. It fundamentally seeks illegal gains or disrupts the order of the online ecosystem. Currently, cryptocurrency and crypto industry infrastructures are deeply integrated into the entire online black and grey market ecosystem.
Traditional Internet black and gray activities now integrate crypto into illegal activities or replace original technical methods with crypto tools, enhancing the deception and destructiveness of certain illegal activities and reducing the chances of being detected or sanctioned by government departments. New types of activities in the blockchain black and grey market directly target the crypto assets of crypto investors or institutions, constituting native criminal activities in the crypto industry.
This report only discloses part of typical activities that utilize crypto in blockchain black and grey market.
2.3 Money Laundering
Money laundering refers to the act of legitimizing illicit proceeds, mainly disguising and concealing the origin and nature of illegal income and its profits through various means to make them appear legitimate. These activities include providing fund accounts, assisting in the conversion of property forms, and assisting in transferring funds abroad. crypto, especially stablecoins, have been used in money laundering activities from an early stage due to their low transfer costs, geographically unbound nature, and certain censorship-resistant features that are one of the main reasons for the criticism of crypto.
Traditional money laundering activities often use the crypto over-the-counter market for exchanges between fiat and crypto. The scenarios and forms of laundering vary, but the essence of such activities is to block law enforcement officers from tracking the money trail, including traditional financial institution accounts or crypto institution accounts.
Unlike traditional money laundering, new forms of crypto laundering target crypto themselves, and crypto industry infrastructures like wallets, cross-chain bridges, and decentralized trading platforms are illegally utilized.
3. Use of cryptocurrency in Online Gambling Activities
3.1 The Use of Cryptocurrency in Traditional Online Gambling Platforms
In recent years, it has become quite common for online gambling platforms and their agents to use crypto. Here are some examples:
Some online gambling platforms have independently established a centralized management system for crypto deposits, transactions, and withdrawals. Gamblers purchase cryptocurrency (mainly USDT) on third-party platforms and transfer it to each gambler’s deposit address assigned by the online gambling platform to acquire chips. Based on a withdrawal request from a gambler, the platform transfers funds from a unified hot wallet address to the target address, which is consistent with mainstream crypto trading platforms.
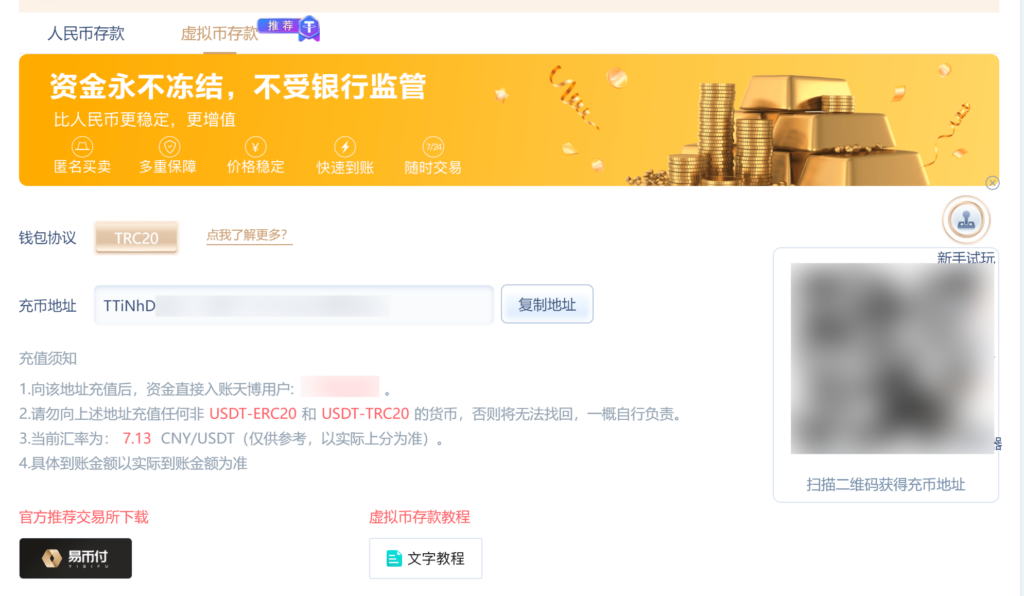
Some online gambling platforms provide channels for deposit and withdrawal for gamblers by integrating crypto payment tools. Gamblers do not directly deposit USDT to the online gambling platform but transfer funds to the payment platform’s account. The latter also satisfies withdrawal requests. The online gambling platform and the payment platform regularly settle funds.
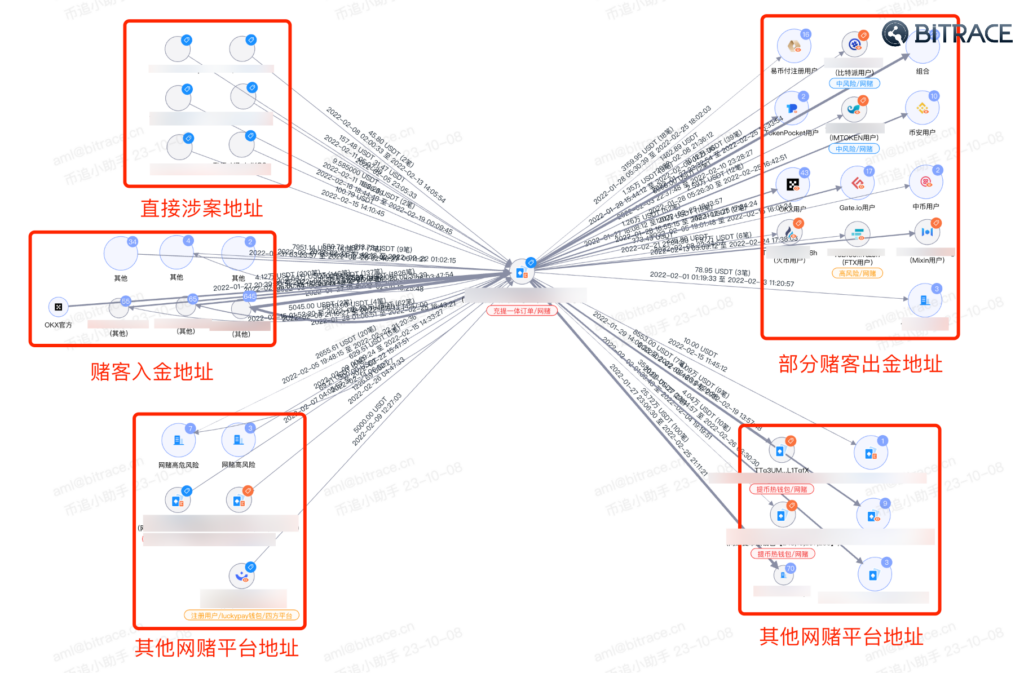
Taking a betting platform that accepts USDT as an example, this platform helps gamblers who have USDT deposits and withdrawals via a crypto payment platform. Bitrace tracked one hot wallet address of this platform and found that this address processed over 1.332 million USDT in deposit and withdrawal order requests from gamblers from January 27 to February 25, 2022.
In practice, although some top online gambling platforms tend to build their own crypto deposit and withdrawal functions, the small and medium-sized platforms choose to rely on other crypto payment platforms. According to the DeTrust platform that focuses on fund risk tracking and auditing, from September 2021 to September 2023, over 46.45 billion USDT flowed directly into traditional online gambling platforms or crypto payment platforms that provide deposit and withdrawal services for them.
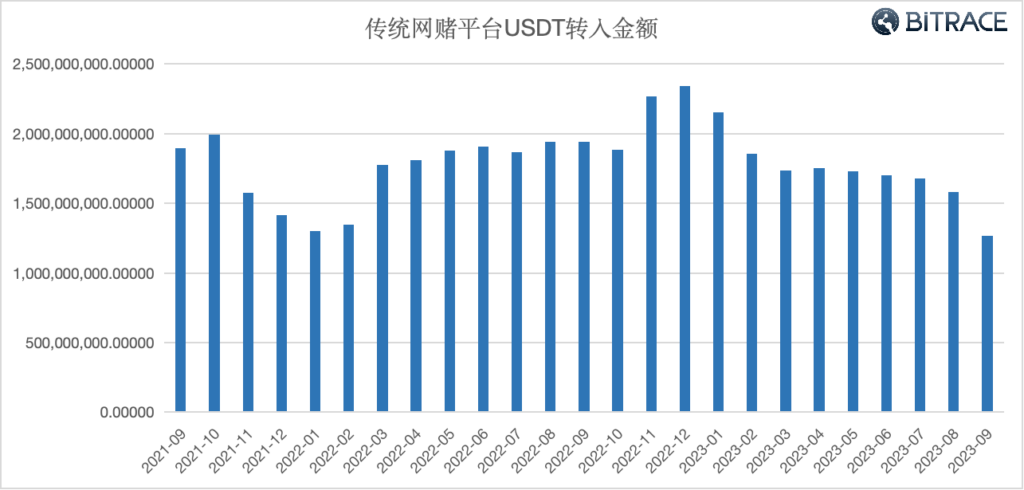
The change in the scale of online gambling funds in 2021 corresponded to the development of the secondary market for crypto that year. From November 2022 to January 2023, the increase in the funds might be associated with many betting activities during the World Cup.
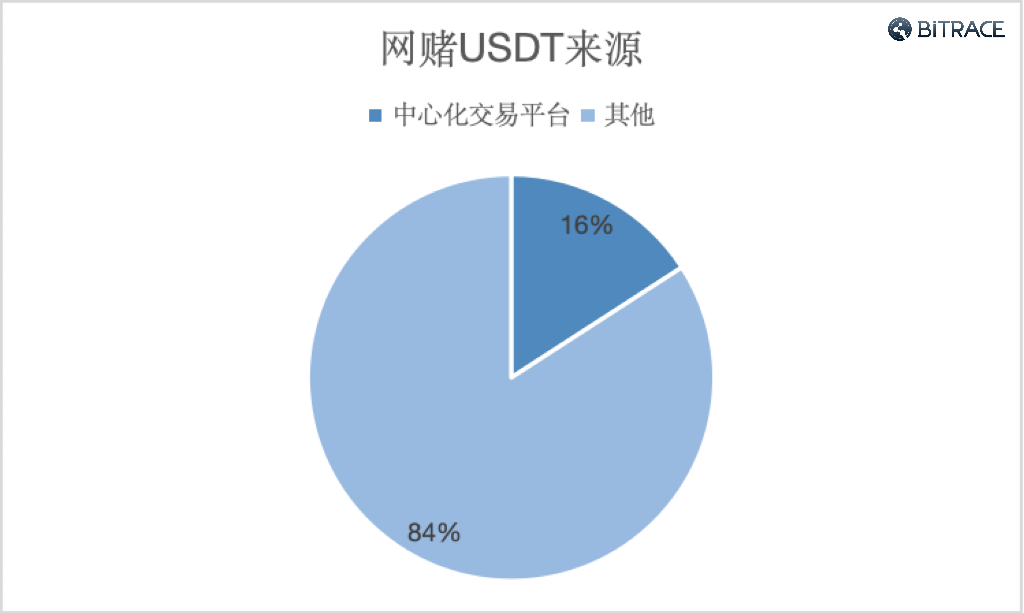
Analyzing the sources of USDT transferred to online gambling platforms reveals that over 8.34 billion USDT came directly from centralized trading platforms, accounting for 16% of the total inflow. These funds came directly from exchange addresses to online gambling platforms or were from casinos and their agents through trading platforms. Considering that there are also funds that came from centralized trading platforms, this figure is a gross underestimate. It indicates that centralized crypto trading platforms serve the online gambling industry.
3.2 New Forms of Hash-based Online Gambling
Every transaction on the blockchain corresponds to a unique hash value, randomly generated and impossibly fake. Hence, a large number of online gambling platforms have developed hash-based betting games. The rules involve guessing whether the last or several digits of the transaction hash are odd or even, big or small, to determine the outcome of the bet and divide the stakes.
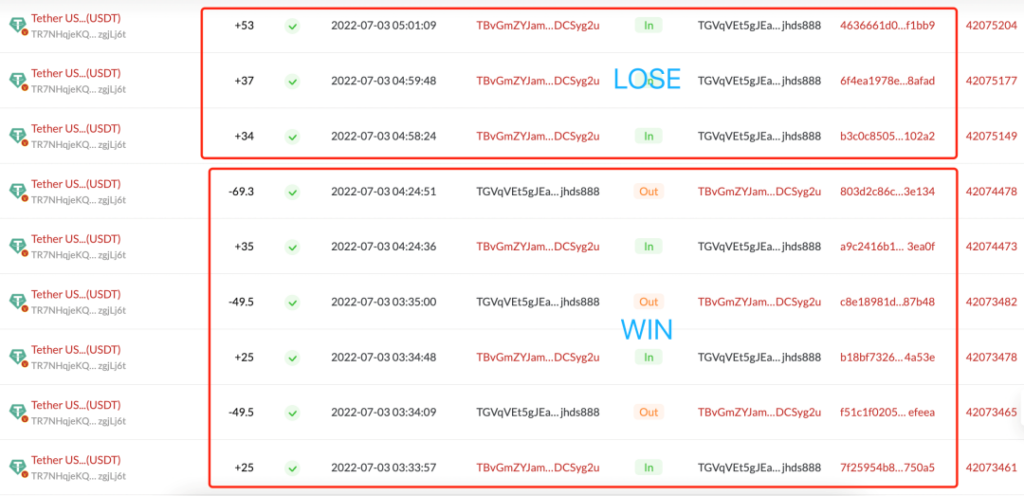
For example, in the typical “Guess the Tail Number” game, gamblers initiate a transfer to the betting address. If the tail number of the hash value of the transfer is a specific number or letter, the gambler wins, and the platform returns double the chips after deducting a certain percentage; if the tail number is incorrect, the gambler loses, and the chips are lost.
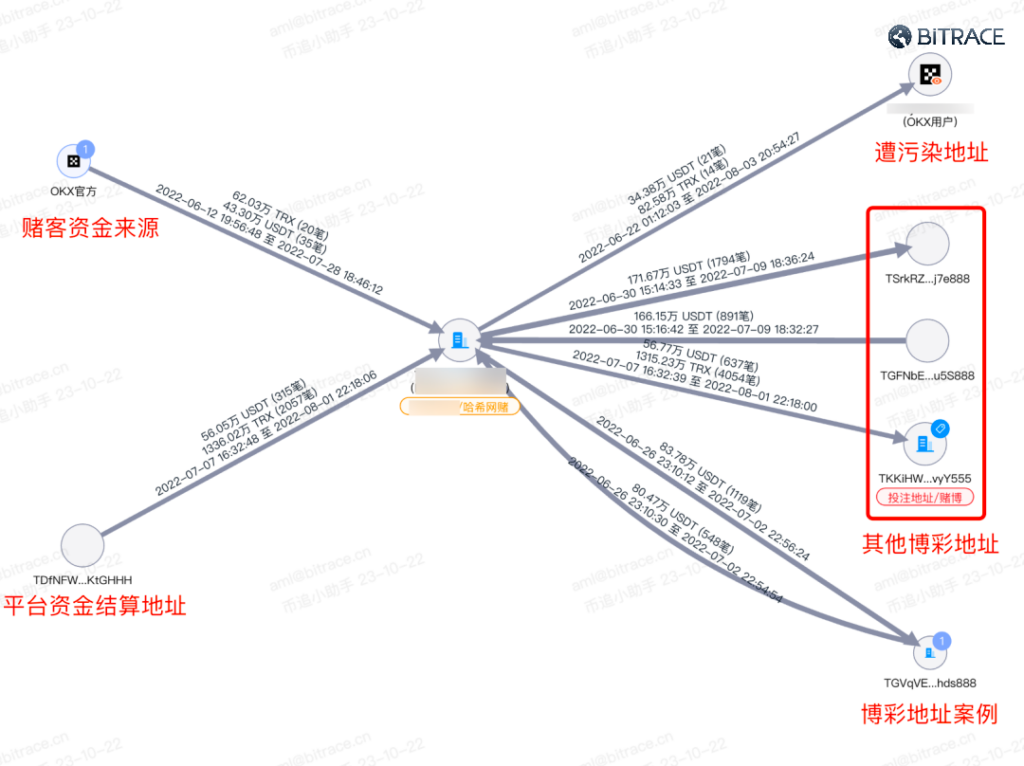
As a result, these online gambling addresses on the blockchain often show high-frequency, fixed-amount financial interactions with multiple addresses, leading to a massive scale of fund interactions.
Finally, these hash-based online gambling games, known for their fast pace and fair play, were once popular, spawning variant games and platforms. However, due to the overly transparent nature of the gameplay and the ease with which funds can be hacked and stolen, the scale and market share of such games have significantly decreased.
4. Use of cryptocurrency in Activities of Black and Grey Market
4.1The Cryptocurrency Use in Traditional Black and Grey Market
4.1.1 Investment and Financial Fraud
Investment or financial fraud is one online investment scam where fraudsters often claim to be “experts in the field” through social media channels. The so-called experts attract victims to fake platforms (usually apps) for investment by building reliable relationships with investors, expressing care, and persuading them, thereby rolling all the investors’ funds. In these fraudulent apps, investors are frauded to invest large sums of money after receiving small or even large profits through investment, gambling, buying and selling goods, trading securities, etc., with most or all of the loss of their funds eventually. Victims realize they are frauded when they cannot “withdraw” funds from the app and contact the so-called “experts” as well.
This traditional online investment scam has also integrated cryptocurrency or crypto tools into fraud in recent years, such as romantic scams and USDT laundering scams.
4.1.1.1 Romantic Scam
The romantic scam often combines with investment fraud, but its primary victims are not crypto users. The fraudsters create perfect online images and use online romantic relationships to induce their romantic partners to purchase USDT and participate in crypto investments, such as currency exchange arbitrage, derivative trading, liquidity mining, etc.
At first, victims’ “investments” earn a lot, so they are encouraged to invest more. However, the victims’ USDT does not participate in the so-called arbitrage activities but is transferred out and laundered as soon as it enters the platform. The platform refuses withdrawal requests for various reasons until the victims finally realize they have been frauded.
4.1.1.2 USDT Laundering Scams
USDT Laundering Scams disguise themselves as money laundering platforms, claiming to be platforms for laundering involved USDT funds. But in reality, they are investment scams. Once participants invest a significant amount of USDT, the platform refuses to return it for various reasons.
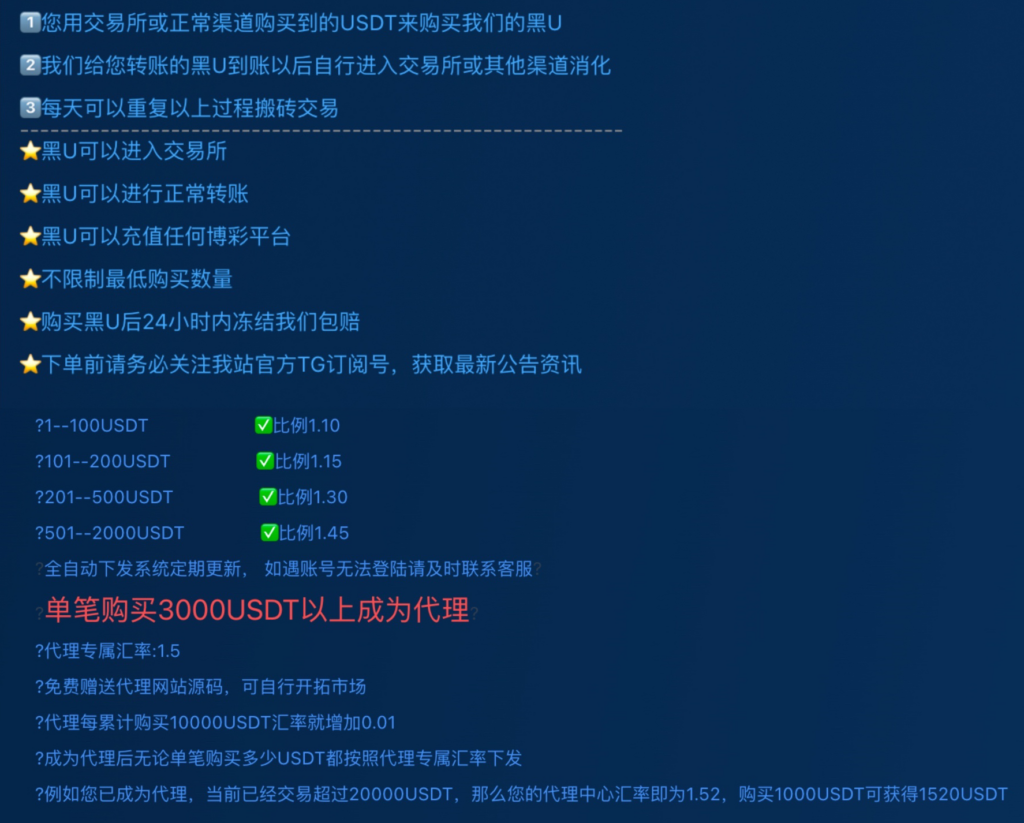
For example, a still-operating “USDT Laundering Platform” allows users to exchange “clean U” for “black U” at an “exchange rate” of 1:1.1~1.45. After receiving the black U, users transfer it to other platforms for sale, with the excess amount being the user’s profit.
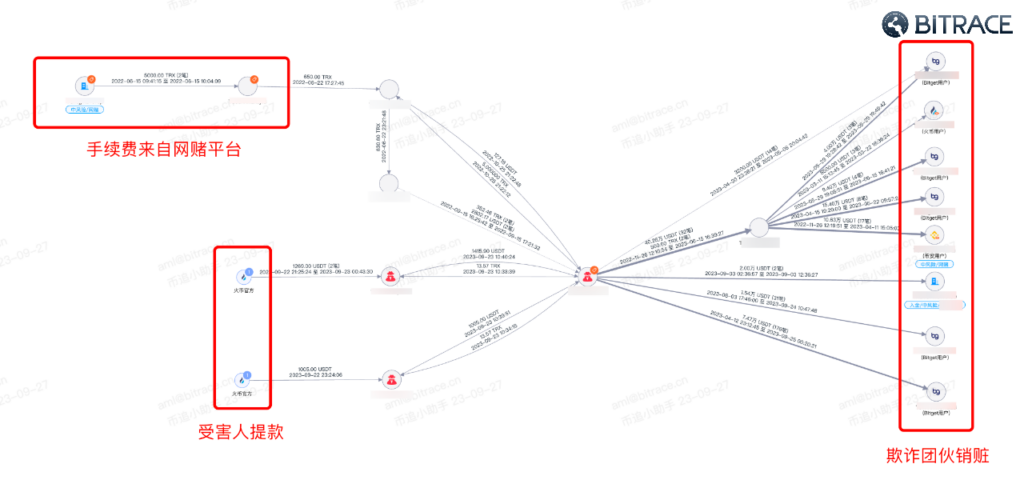
Until now, this fraudulent group has illegally obtained over 870,000 USDT using the same method. 784 independent addresses have transferred USDT to the fraudulent address, but only 437 addresses have received repayments, with nearly half of the participants failing to gain “arbitrage.”
4.1.2 Fake APPs
Fake Apps refer to apps where criminals repackage genuine apps to deceive users. Fake apps combined with crypto mainly include fake wallets and fake Telegram apps.
4.1.2.1 Fake Wallet APP
Fake wallet app theft is a method where thieves induce others to download and install illegal wallet apps with backdoors to steal wallet mnemonic phrases and illegally transfer other people’s assets. The thieves distribute fake wallet app download links through search engines, unofficial mobile app stores, social media platforms, etc. Once victims download, install, and create or sync wallet addresses, the mnemonic phrases come into the thieves. When the victim transfers a large amount of cryptocurrency into the fake app, the thieves will transfer the money into their own pocket.
This method has become highly industrialized. Fake wallet development companies and operational promotion teams are totally separated; the former only participates in product development and maintenance, selling product solutions worldwide. The latter is responsible for promoting the fake wallet app, even without understanding the principles of crypto technology.

Multi-signature theft is a variant of the traditional fake wallet theft. Multi-signature technology involves multiple users signing a digital asset simultaneously. If an address can only be signed and paid by one private key, it is expressed as 1/1, while multi-signature is expressed as m/n, meaning that a total of n private keys is for an account, and the transaction is permitted when m addresses sign.
Traditional fake wallet theft essentially shares wallet control with the victim so thieves cannot prevent the victim from transferring assets. However, based on multi-signature technology principles, thieves immediately add the victim’s address to multi-sign after the victim installs the fake wallet app. The wallet owner then cannot transfer assets in the wallet but can only make deposits. Thieves can transfer the assets at any time, usually depending on the amount of money.
4.1.2.2 Fake Telegram APP
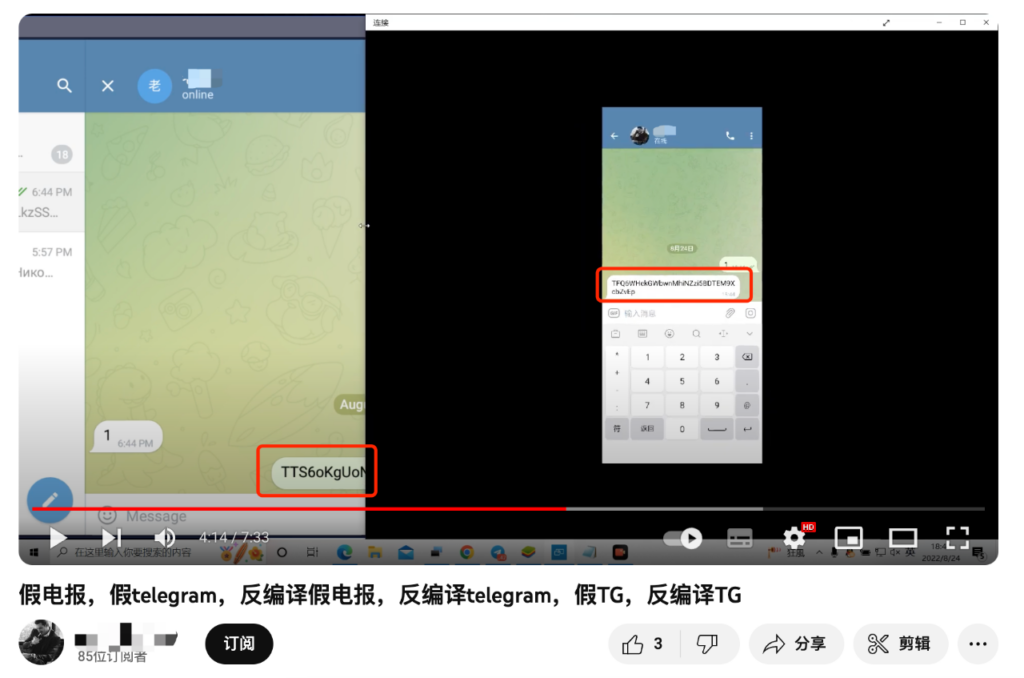
A classic application of fake apps in crypto-related black and grey industries is the malicious backdoor implantation of the Telegram app, a social software commonly used by crypto investors, with many over-the-counter trading activities relying on it. Fraudsters use social engineering attacks to induce targets to “download” or “update” fake Telegram apps. Once the target user pastes a blockchain address in the chat box, the malicious software recognizes and replaces it with a malicious address, causing the counterparty to send funds to the malicious address unknowingly.
4.1.3 Third-Party Payment Guarantees
Third-party payment guarantee refers to the process in which the buyer firstly pays the money to a third party that temporarily holds it. Once the buyer receives and checks the goods and notifies the third party, the third party pays the seller, completing the transaction. It involves a third party acting as a credit intermediary, temporarily overseeing the funds until the buyer confirms receipt of the goods. During this transaction process, the third-party intermediary charges a service fee.
Currently, some third-party payment guarantee platforms focusing on black and grey markets, in addition to traditional fiat channels, have started to commonly use Tether (mainly trc20-USDT) as the guarantee funds, providing payment guarantee services for transactions that include illegal currency exchange, illegal goods trading, illicit collection and payment services, and crypto transactions. Despite different transaction types, the transaction process is consistent.
Typically, the buyer or seller pays for ads about the payment guarantee platform in some specific websites, or the official Telegram group. The ads detail the type of transaction, requirements, payment methods, and other specifics.
After the buyer and seller’s negotiation, they rely on the platform’s customer service to set up a “dedicated group,” a private Telegram group used exclusively for transaction communication, including the buyer, seller, and bot. In principle, one-to-many transactions are not allowed, nor is the inclusion of unrelated individuals.
The buyer must transfer the payment to the official account of the guarantee platform and provide proof. After the transaction officer confirms the receipt, they notify the seller to ship the goods. The seller then delivers the goods via ships and provides proof of shipment. The buyer will confirm receipt and t hen the transaction officer will release the funds. Upon receiving confirmation of receipts or instruction to release funds from the buyer, the transaction officer deducts a commission and releases the funds to the seller, providing proof of payment. Finally, the seller confirms receipt of the funds so
the transaction is complete.
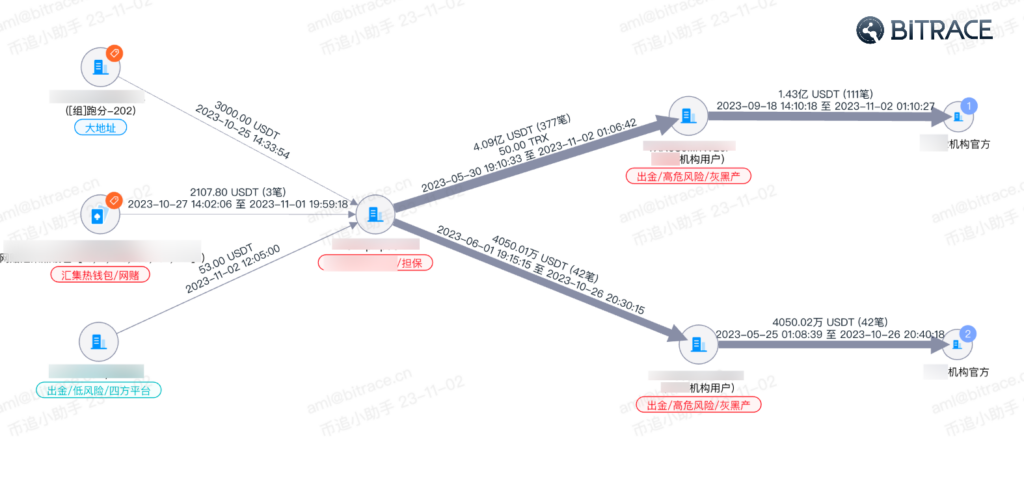
The platform does not assign a separate address for each transaction for fund isolation. Instead, all deposits within a certain period are sent to the same deposit address, resulting in this address directly receiving a large amount of funds involved in online gambling, black and grey market, and money laundering. The large scale of funds also obscures the direction of funds, creating obstacles for investigators tracking these activities.
Auditing a group of platform addresses that guarantee illegal transactions revealed that the scale of their guarantee funds has been growing over the past 12 months. All the addresses include over 17.07 billion USDT on the Tron network and over 670 million USDT on the Ethereum network, indicating that most of the illegal transactions guaranteed by these platforms occur on the Tron network.
4.2 The Cryptocurrency in New Forms of Black and Grey Market
4.2.1 Token Approval Theft
Token approval theft is illegal getting assets by acquiring management rights to another USDT address. Public chains like Tron and Ethereum allow users to transfer operational rights of certain assets in their wallets to other addresses and gain partial or complete management rights over the assets in that address.
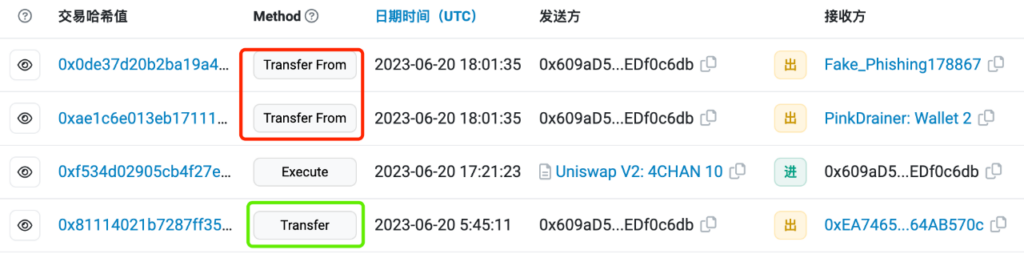
This malicious currency theft is like a payment link, airdrop claim entrance, and other methods. Once the victim starts to interact, some asset in the address – usually USDT – will be lost later.
Thieves typically achieve this by tricking the target into clicking phishing links and running fraudulent smart contracts. As the victim’s wallet mnemonic phrase is not in this process, prompt revocation of authorization can mitigate some losses.
4.2.2 Zero-transfer Phishing
Zero-transfer phishing is a scam targeting crypto investors who use wallet uncarefully. By sending a large number of zero USDT transactions to unspecified blockchain addresses, the scam increases the interaction records of the target address. If the phishing link successfully copies an address from existing transfer records on a smart device while transferring to an address, it may send funds to the wrong address, resulting in losses.
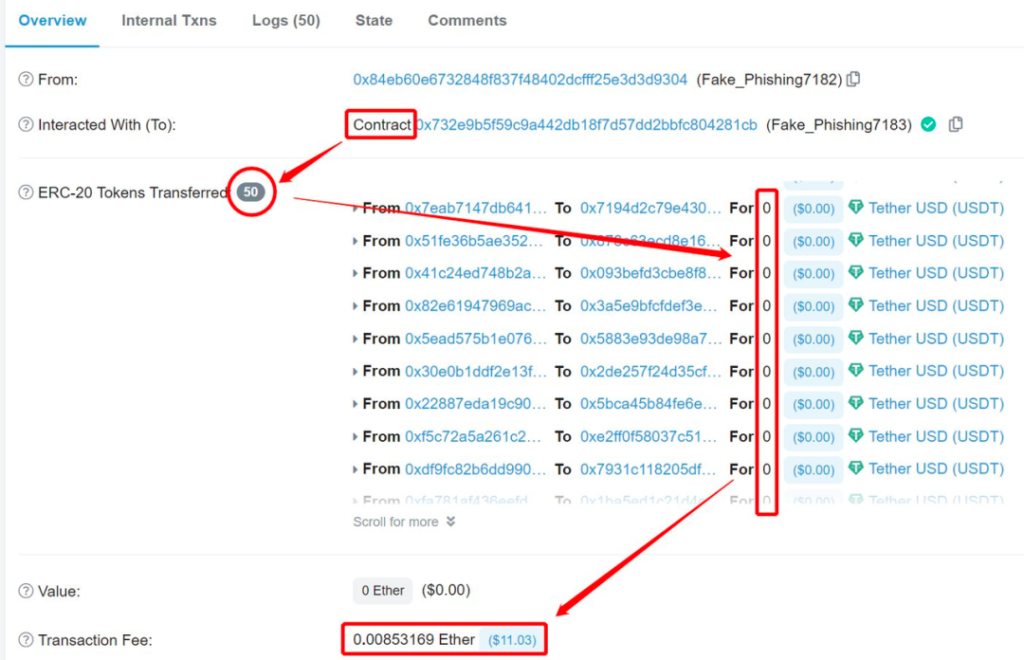
Bitrace analyzed many addresses on the Tron network marked as phishing addresses, defining transactions with less than 1 USDT as illegal activities and over 10 USDT as fraudulent gains.

Our research shows that the activity and scale of zero-transfer phishing are continuously expanding. Until now, over 451 million USDT were lost in the Tron network due to phishing attacks.
4.2.3 Fake Crypto Arbitrage Scams
A common tactic in fake crypto arbitrage scams involves fraudsters falsely claiming to have developed an illegal “smart arbitrage contract.” Participants invest a certain amount of cryptocurrency into the contract, promising them an excessive return in another well-known crypto (such as Binance Coin, Huobi Token, OKB, etc.). Once they receive the “arbitrage gains,” participants can sell these on a third-party trading market to earn profits.
During early small-scale tests, participants receive real excess cryptocurrency. However, once victims invest more sums, they are returned fake tokens, which have no market value. This ancient yet effective method of fraud is still widely used in the crypto investment community, causing financial losses for ordinary investors and damaging the brand assets of those impersonated by the fraudsters.
4.2.4 Vanity Addresses Trading
Just like criminals in traditional activities in the black and grey market, the blockchain criminals need to create or purchase virtual identities before engaging in illegal activities. In crypto activities, they use blockchain addresses rather than traditional bank accounts and personal identities. Usually, these addresses are custom-made by professional virtual address service providers.
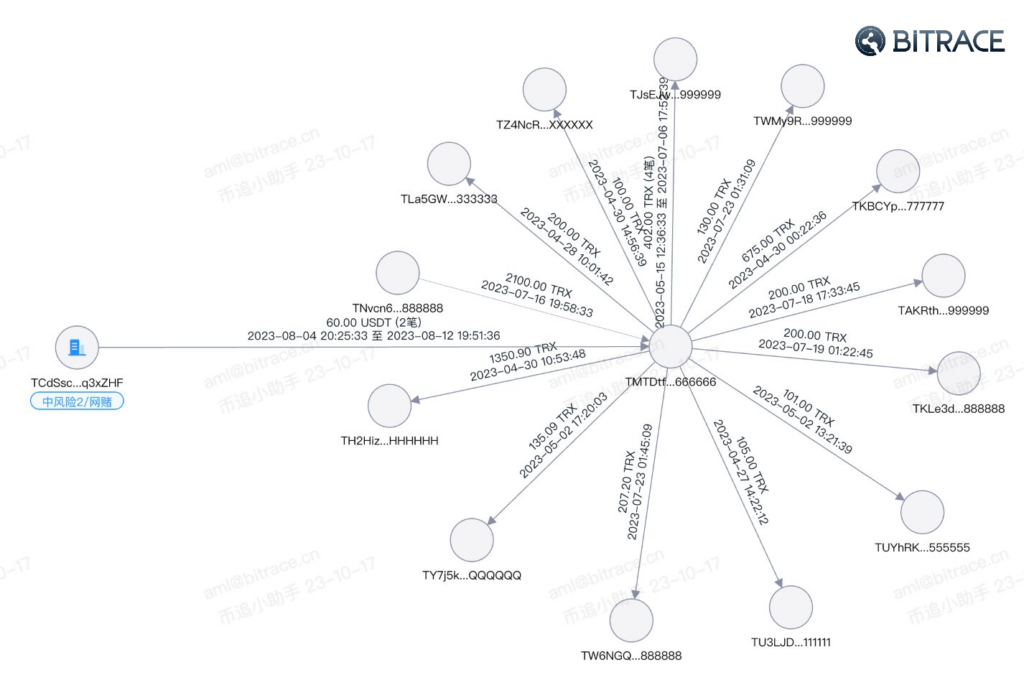
In online gambling activities, operators of hash-based online gambling platforms often use virtual addresses on the Tron network. They purchase these virtual numbers in bulk from professional service providers and use them as business addresses for various purposes, including receiving and making payments, storing and circulating funds, accepting bets, and settling funds.
In crypto activities, the virtual addresses have led to more sophisticated operational variants of zero-transfer phishing—tail number phishing. Unlike regular zero USDT transfers targeting unspecified blockchain entities, tail number phishing is customized. Fraudsters create high-fidelity imitations based on the head and tail numbers of addresses frequently used by their targets and transfer more money.
The cost of these phishing activities is not low. According to a price list from a Tron virtual address service provider, a customized eight-digit address takes 12 hours to deliver and is priced at 100 USDT, while a similar eight-digit virtual number costs only 10 USDT.
Apart from Tron virtual address service providers, there are four different services: (1) chatbot service in Telegram app group (2) source code service of websites (3) batch transfer tool service (4) SEO rapid ranking service, which similarly assist perpetrators in illegal activities and profit from it. This report will not disclose more on this topic.
5. Use of cryptocurrency in Money Laundering Activities
5.1 The Cryptocurrency in Traditional Money Laundering
The use of cryptocurrency in traditional money laundering aims to transfer payments from high-risk users to low-risk users’ accounts, thereby circumventing the risk control measures of payment institutions. This typically manifests as exchanging incriminated fiat currency for crypto in the crypto over-the-counter market, or vice versa, to break the funding chain and evade tracking and crackdown.
A typical money laundering scenario involves fraudsters rapidly splitting the cash obtained from victims into small, consecutive transfers to multiple bank cards. Then, “card farmers” withdraw the cash, which is subsequently transported to the laundering gang’s location by personal or public transportation means like cars or airplanes. In the past, this cash was often used to purchase bulk commodities or exchange for foreign currency to leave the country. Now, it is more commonly used to buy USDT offline, which is then either cashed out in the crypto over-the-counter market or directly transferred abroad or to other laundering gangs for further processing. In this process, platforms like USDT laundering platforms, payment guarantee platforms, and centralized exchange over-the-counter markets play an important role.
5.1.1 USDT Laundering Platforms
“USDT laundering platforms”are a new form of money laundering, combining digital currency trading on traditional “Laundering” platforms. First, the platform organizer lures USDT movers with the bait of buying USDT in bulk to sell at a higher price on foreign exchanges. The movers register a digital currency exchange account with their real names and link their bank cards. They must buy a certain amount of USDT as a trading margin to pledge to the “Laundering” platform. The organizer then sets up an account for the mover on the platform, marking the amount and price of USDT available for sale, while noting the mover’s bank account information for receiving payments. When overseas telecommunication fraud gangs need to receive illicit funds, they order USDT from movers through the “Laundering” platform and direct victims to transfer money to the mover’ bank accounts reserved on the platform. Once the victims transfer the scammed funds to the mover’s account, the mover confirms the transaction on the platform, completing the first transfer of the fraud funds. The mover then uses the illicit funds to continue buying USDT from the exchange, withdrawing it to the Laundering platform and earning a difference in USDT prices and platform commissions.
This activity is called “From card to U” by laundering gangs, helping upstream criminals and laundering gangs evade the risks of illicit funds and exchange platform identity verification.
5.1.2 Laundering Fleets
Besides recruiting individuals for money laundering, launderers often use a more direct “Laundering fleet” model. The form is similar to the USDT laundering model, but what differs is that the crypto over-the-counter transactions occur offline and are in cash. First, the fleet leader recruits numerous individuals to register real-name bank card accounts. When upstream criminals (the so-called “material masters”) illegally obtain illicit funds (the so-called “materials”), they contact the fleet leader to take orders through illegal third-party payment guarantee platforms. The funds are then split and transferred to multiple bank cards controlled by the fleet. If the money is first-hand black money, it is called “first-hand material.” If it’s second-hand or third-hand black money, it is correspondingly called “second-hand material” or “third-hand material,” with lower risks and commissions for the latter. The fleet leader then drives with the cardholders to local ATMs for multiple cash withdrawals. After completing the withdrawals, the fleet leader continues to use personal or public transport to take the cash to a designated location for offline transactions. Finally, with the involvement of a third-party payment guarantee platform, the fleet leader hands over the money to the target entity to earn a commission. The other party transfers USDT to the guarantee address to end the laundering process.
This type of laundering activity, involving multiple bank account transfers, ATM withdrawals, and offline crypto transactions, breaks the funding tracking chain and evades bank fund supervision.
Bitrace conducted a funds audit on a group of addresses in the Tron network marked as money laundering risks with a fund scale that exceeds 1 million USDT. The audit period was from September 2021 to March 2023, focusing on USDT inflows.
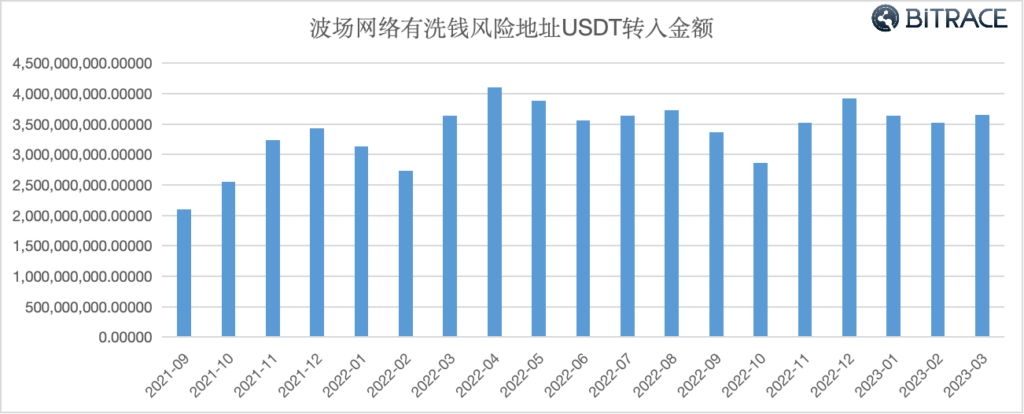
Data shows that from September 2021 to March 2023, addresses in the Tron network with money laundering risks had an inflow of over 64.25 billion USDT. The fund was not influenced by the bear market in the secondary crypto market, indicating that the participants in these activities are not genuine investors.
5.2 The Crypto Currency in New Forms of Money Laundering
Cybercriminals in the crypto industry, exchanges based on crypto infrastructure and on-chain obfuscation are the most common way of money laundering.
5.2.1 On-chain Fund Obfuscation
On-chain fund splitting and mixing platforms are the most prevalent for fund obfuscation.
Fund splitting refers to criminals using complex, multi-layered transactions to blend virtual currencies through various wallet addresses and accounts, eventually transferring them to the wallets of overseas accomplices. This method severs the link between fund input and output and obscures the virtual currency transaction chain. In crypto money laundering activities, this is equally effective and is a popular method by practitioners in the black and grey market.
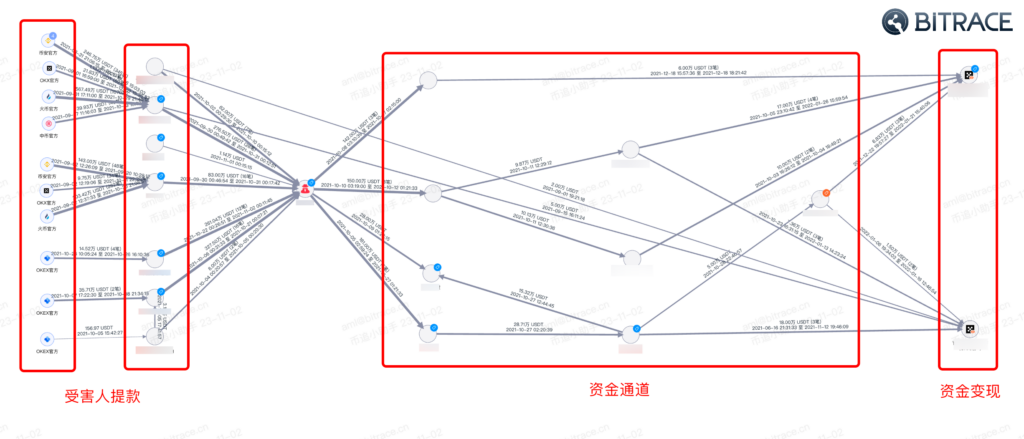
For instance, in one investment and finance scam, the funds from victims were split through several channels and ultimately consolidated into a few exchange account addresses for cashing out.
Mixing involves combining the users’ cryptocurrency with other users’ digital assets and transferring the mixed funds to a target address. This process masks the original flowing path, making it difficult to trace the origin and destination of the cryptocurrency. As a result, several crypto-mixing platforms have been sanctioned by governments worldwide, including the well-known Tornado cash. This platform was punished by the U.S. Department of the Treasure’s Office of Foreign Assets Control (OFAC) on August 8, 2022, with some associated Ethereum addresses being placed on the U.S. Specially Designated Nationals list. Being added to this list means individuals or related entities with the risk of having their properties and property interests frozen.
However, despite this, since Tornado Cash’s mixing contract is public and permissionless, other users can still conduct mixing activities by directly invoking the contract. For example, in the Onyx Protocol attack on November 1, 2023, the attacker obtained transaction fees through a mixing platform and further laundered the funds.
5.2.2 On-chain Anonymous SWAP
No-KYC trading platforms and cross-chain bridges are the two primary channels for on-chain anonymous exchanges.
Until now, apart from a few sanctioned entity addresses, these crypto infrastructures have not imposed more risk control on risky cryptocurrency or high-risk crypto addresses. As a result, after an attack occurs, illicit funds often quickly utilize these channels for exchange.
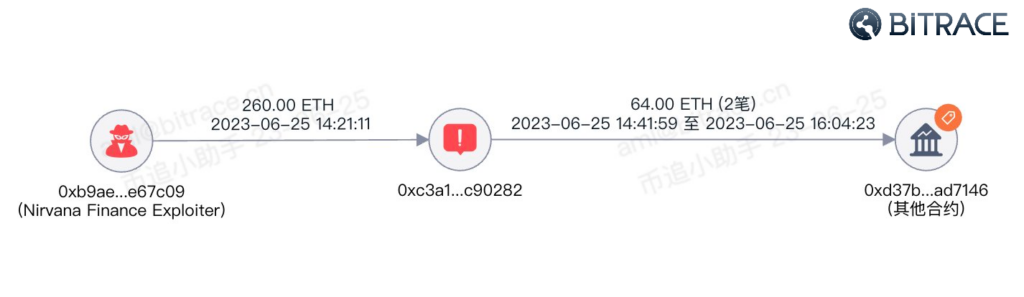
For instance, in the Nirvana Finance attack on June 25, 2023, the attacker immediately transferred a portion of the illegally obtained crypto to THOR Wallet DEX after the attack. THOR Wallet DEX is a permissionless and highly private decentralized exchange platform which allows users to conduct cross-chain exchanges between blockchains without disclosing transaction information. Thus, in many crypto security incidents, THOR Wallet DEX has appeared in the fund laundering process.
6. The Contamination of Risky Crypto in Web3 Business Addresses
6.1 Contamination of Centralized Trading Platform Addresses
Centralized trading platforms are one of the primary venues for laundering risk USDT funds. In this report, Bitrace audited the hot wallet addresses of 126 common centralized trading platforms, thoroughly examining the inflow of crypto associated with online gambling, activities in black and grey markets, and money laundering from January 2021 to the present.
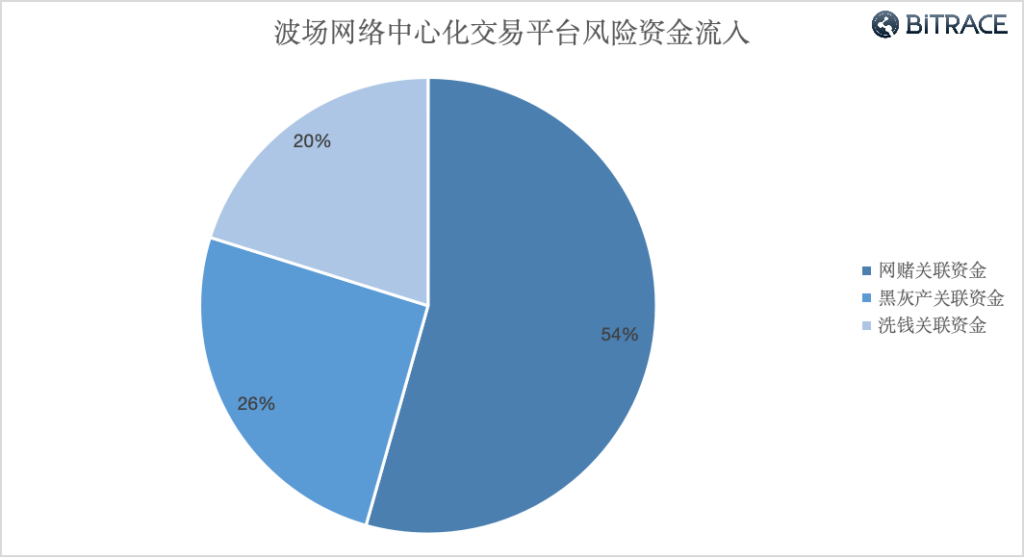
From January 2021 to September 2023, over 41.52 billion risk USDT flowed into some centralized trading platforms on the Tron network, including 22.579 billion USDT related to online gambling, 10.57 billion USDT related to activities in the black and grey market, and 8.373 billion USDT related to money laundering.
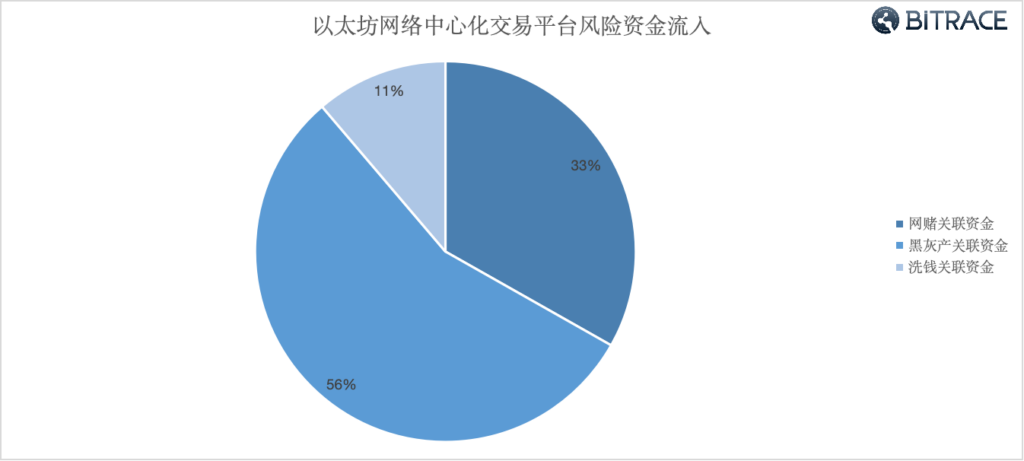
During the same period, on the Ethereum network, over 3.315 billion risk USDT flowed into some centralized trading platforms, including 1.1 billion USDT related to online gambling, 1.842 billion USDT related to activities in the black and grey market, and 372 million USDT related to money laundering.
The total amount and proportion of risk funds indicate that the scale of illicit USDT utilization in the Tron network is larger than that in the Ethereum network, with a higher proportion of risk funds related to online gambling. It could suggest that, in practice, casino agents and gamblers prefer Tron USDT to save on transaction fees.
6.2 Contamination of Over-the-Counter Market Addresses
Apart from the over-the-counter trading sections of centralized trading platforms, several payment platforms, crypto investor groups, and exchanger communities establish sizeable over-the-counter markets. These parties lack comprehensive KYC and KYT mechanisms, cannot assess the risk of counterpart funds, and struggle to restrict risk funds post-transaction, often resulting in a higher proportion of risk USDT inflow.
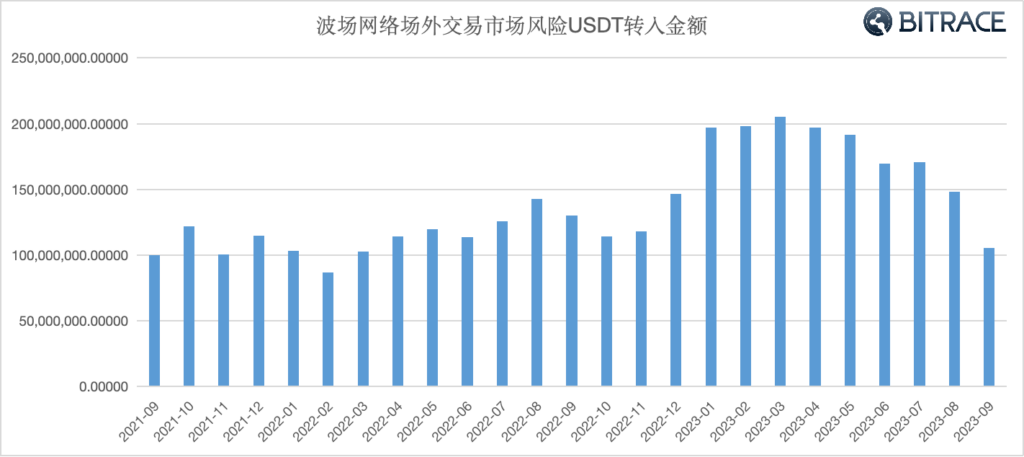
Bitrace audit addresses with typical characteristics of the over-the-counter market and a fund scale exceeding 1 million USDT. The data shows that addresses have received at least 3.439 billion USDT associated with risky activities over the past two years,
As one of the infrastructures in the decentralized finance field, crypto payment tools provide fund settlement services for blockchain institutions and crypto acceptance services for ordinary users, thus facing the same risk of contamination by illicit crypto.
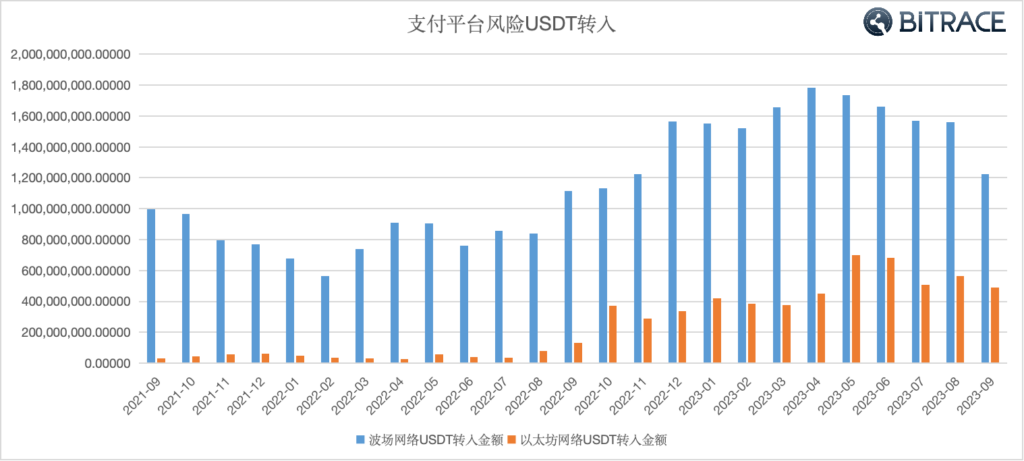
Bitrace audited the addresses of main crypto payment platforms which serve Southeast Asian and East Asian customers. Data shows that, from January 2021 to September 2023, over 40.51 billion risk USDT flowed into these addresses, with 33.46 billion USDT on the Tron network and 7.04 billion USDT on the Ethereum network. Throughout almost all periods, the contamination of crypto payment platforms by risk USDT in the Tron network is comparatively more severe than that in the Ethereum network.
7. Conclusions and Recommendations
Participants in online gambling, activities in the black and grey market, and money laundering are increasingly utilizing crypto, including USDT, to enhance the anonymity of funds and evade tracking by regulatory and law enforcement agencies. As a direct consequence, Web3 enterprises that operate compliant crypto businesses and ordinary crypto investors, lacking the ability to identify risk, inadvertently receive cryptocurrency associated with different risky activities. It leads to contamination of their fund addresses and the risk of getting involved in illegal cases.
Industry institutions should strengthen their awareness of fund risk control, actively cooperate with local law enforcement, and integrate threat-predicting services provided by security vendors. It will enable them to identify, prevent, and block risky crypto, thus protecting their business and user addresses from contamination.
7.1 Strengthening Fund Risk Control Awareness
Beyond the basical Know Your Customer (KYC) activities – legally verifying customers’ real identities, transaction execution, and sources of funds – industry institutions should also fulfill their duties to monitor and manage unusual customer transactions (KYT). They should promptly report illegal transactions and risk situations for users who are involved in suspicious risk fund activities. Meanwhile, tiered management, including restricting some or all platform functionalities, should be applied, .
7.2 Understanding Local Laws and Cooperating with Law Enforcement
Platforms should have professional teams to handle and review global law enforcement requests, assisting in identifying, combating, and preventing crypto-related criminal activities. It will reduce economic losses and prevent addresses and user accounts from being contaminated by illicit funds.
7.3 Establishing a Threat predicting Network and Information Sharing Mechanism
Crypto institutions need to pay attention to open-source network intelligence, keeping an eye on risky addresses and funds related to current crypto security incidents to ensure timely countermeasures against implicated funds. They should also integrate external threat-predicting sources and collaborate with crypto data and security companies to build reliable criminal profiles. The control of risk should be applied to addresses that could be risky and lack a good interaction history. On this basis, an open, industry-wide threat-predicting database should be built and maintained to ensure the overall security and trust of the industry.
8. About Us
Bitrace is a blockchain security company that provides leading crypto data analysis, risk management, and law enforcement collaboration tools and services for Web3 enterprises, financial institutions, and regulatory and law enforcement agencies. The company has already launched two products: DeTrust and Bitrace Pro.
DeTrust is built based on a leading criminal database, fund monitoring and early warning capabilities. It forms a collaborative platform involving security companies, trading platforms, service institutions, and law enforcement agencies. This platform facilitates the rapid identification, early warning, interception, freezing, and recovery of criminal funds.
Bitrace Pro offers service like transaction queries, visual analysis, entity identification, and address clustering for mainstream cryptocurrencies like BTC, ETH, USDT-ERC20, and USDT-TRC20. Equipped with over 20 common risk intelligent analysis models, it helps clients swiftly conduct risk event restoration and fund analysis.
We aim to use data analysis technology to identify illegal crypto and, by establishing a collaborative platform, to excavate, warn, intercept, and recover criminal funds. Our goal is to enhance transparency, compliance, and security of applications in blockchain industry. By promoting mutual trust and transparent collaboration among governments, institutions, and enterprises, we aim to help governments and businesses collectively address regulatory and compliance challenges, fostering the compliant and rapid development of the Web3 industry.


