By Sputnik Meng, Chief scientist at Fox Tech; Frederick Kang, CEO of Fox Tech
Preface
Layer1, as a distributed system, requires high communication costs in order to reach consensus, and a lot of computing will also consume expensive gas. Therefore, as an extension of Layer1, the design of Layer2 can effectively improve the efficiency of Layer1. But from this perspective, Layer2 still faces the same challenge as Layer1, which is how to balance decentralization and efficiency.
zkRollup is a promising Layer2 expansion solution by moving computing down the chain and providing zero-knowledge proofs to the Layer1 chain. In the scheme of implementing zkRollup, FOX system adopted the current mainstream structure and mainly had two kinds of nodes, namely Sequencer and Folder. To put it simply, Sequencer is responsible for sorting and packaging the transactions submitted by users and updating the status on the Layer2 chain, while Folder is responsible for generating proof for the transactions packaged by Sequencer and submitting them to Layer1.
A meaningful question is whether Layer2’s nodes should be decentralized, and if so, how to design incentives to ensure this. As you can imagine, the inefficient nature of Layer1 is that each node requires a lot of computation and communication in order to implement decentralization. However, Layer2 system is used to decouple the calculation process. If the decentralized mode of Layer1 is still used in this part, Layer2 will be congested for the same reason, so there is a trade-off to be made here.
The design of incentive mechanism is to encourage Layer2 nodes to participate in the maintenance of Layer2 system by adjusting the way Layer2 nodes get incentive commission and balancing the fees paid to Layer2 nodes. In essence, the Layer2 node receives incentive fees from the same source as Ethereum, which is Gas fees paid by users who submit transactions. In this article, we will explore how FOX nodes participate in the system to collect fees and why.
Role of Gas
First let’s review the role of Gas charges in the Ethereum system. The computing resources of Layer1 are limited. When users submit transactions, they will specify the transaction Gas fee, which is basically related to the complexity of transaction execution. On this basis, users who are willing to pay higher Gas fee can obtain the transaction execution with higher priority. The miners’ incentive comes from the sum of the Gas costs of the packaged blocks. In addition, the Gas fee mechanism can effectively prevent malicious contracts (such as infinite circulation) and limit the block size, thus ensuring a certain degree of security.
Therefore, it can be seen that the reasonable utilization of Gas fees is in essence the reasonable scheduling and allocation of computing resources on the chain, and it is also a multi-party game among project parties, miners and users. The design of good incentive mechanism as well as the use and distribution of commission fees are crucial to the operation of the system.
Transaction Onchain Process
Users submit transactions to the trading pool in the FOX system and attach a commission fee to stimulate the FOX node. Then, Sequencer node in the system will capture transactions from the trading pool for packaging order. Here, each packaged transaction constitutes a block of Layer2, and Sequencer needs to perform transaction calculation. Moreover, the calculation results are transmitted to Layer1’s FOX contract. Moreover, Sequencer also needs to save the trade data into ZK-Ringer to ensure the data availability. After that, the sorting results and calculation results of Sequencer are transmitted to the Folder node, which correctly calculates the proof (including the proof aggregation part) and transmits to the contract of Layer1. In this process, the execution result of Sequencer on the transaction will be directly updated into Layer2 after the execution ends, while the time node when the transaction is truly recognized by Layer1 can be regarded as after the verification of Folder.
As you can see, in this process, the initial fee attached by the user covers several purposes:
- ・Commission paid to Sequencer
- ・The handling fee paid to Folder
- ・Sequencer submits the result of the transaction to Layer1’s Gas fee
- ・Sequencer Fees for storing information to ZK-Ringer
- ・Folder to invoke the Gas fee of the contract
To do this, we need to sort out specific mechanisms to incentivize participation.
FOX Incentive System
FOX’s incentive model is relatively novel. Firstly, in order to balance decentralization and efficiency, the roles of nodes are divided into Sequencer nodes, which are responsible for sorting and executing transactions, and Folder nodes, which are responsible for generating proof and aggregation of correctness of transaction execution. The Folder node of FOX adopts a decentralized mode, that is, any FOX miner can access the network to act as a proof generator. In order to encourage more nodes to participate, the Folder that successfully submits the correct proof to the Layer1 contract can be rewarded with tokens. At the same time, in order to avoid computational waste, we point out that not only the first proof submitter can be rewarded, but within a time window and quantity window after the first proof submitter’s successful submission (the specific parameters here will be adjusted according to the system condition), all correct proof submitters can be rewarded.
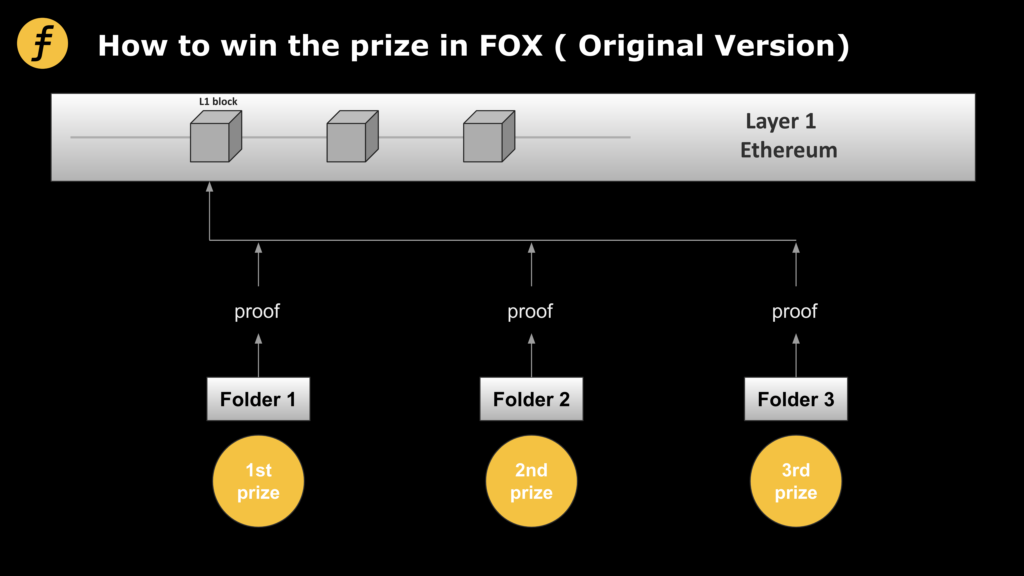
Figure 1: The original incentive model
However, with this mechanism, malicious folders have a sneaky attack.
After a malicious Folder, denoted as Adv, has completed its proifier generation, it submits the proifier to Layer1’s Verifier contract for verification. On the other hand, it colludes with some nodes (or nodes controlled by the Folder) to advertise the computed proifier to those nodes. Then they can not calculate their own directly will calculate good proof submitted, can also receive a part of the reward, and in this process they did not pay any calculation, on the other hand, Adv through less calculation obtained a number of benefits, and cause other nodes even generated the correct proof is difficult to compete for Adv.
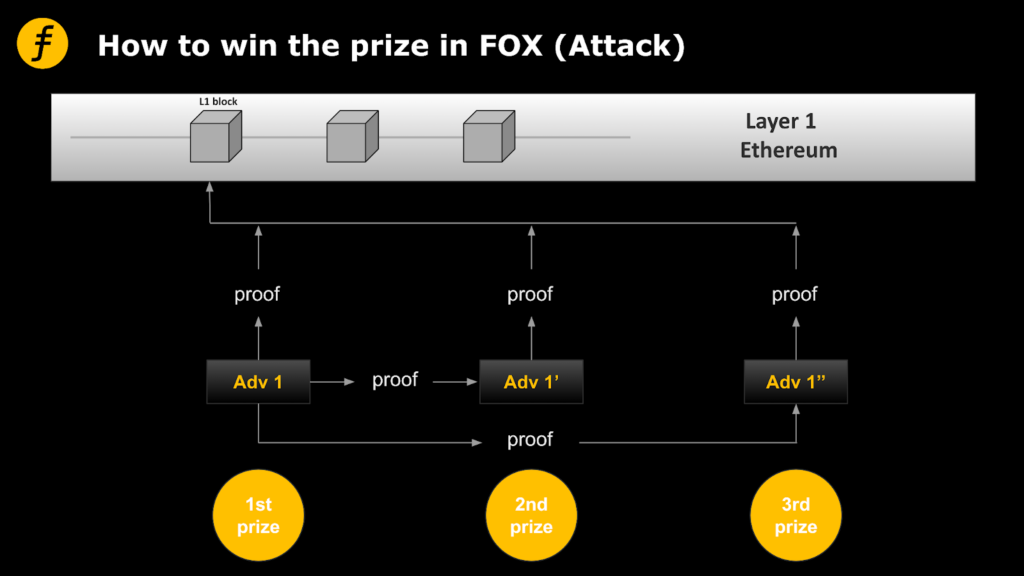
Figure 2: Attack mode of a malicious Folder
In this case, the problem is that the Verifier cannot distinguish whether each certificate is independently generated by the Folder, as the certificate values are all the same. In order to avoid this problem, we need to add the unique address information of folders into the proof of Folder submission, so that the proof of each Folder submission can only be generated independently instead of submitted by other nodes.
There is a clever way to incorporate this information, using Fiat-Shamir heuristic. (See FOX’s previous article, “How to Transform Interactive Proofs into Non-interactive Proofs? Fiat-Shamir Heuristic! For technical details). According to the process of generating the proof, in one step, the prover, namely Folder, needs to generate a random challenge value through the hash function. It only needs to add the address of the Folder into the input of the hash, so as to ensure that the challenge value corresponds to the address of the Folder. Moreover, it is still a random number that cannot be predicted and controlled by Folder.
To strictly explain the security of this method requires more in-depth cryptography, the concept of theoretical security of random function and indiscriminability, and so on, we will not discuss in detail here. Briefly, it can be argued that the security of the original zkp algorithm can still be guaranteed by adding a fixed value as the preimage of the hash without breaking the unpredictability of the output, due to the security of the hash function itself and that of the Fiat-Shamir heuristic structure.
In this way, each Folder would have to be generated independently of the other node results, thus achieving our goal.
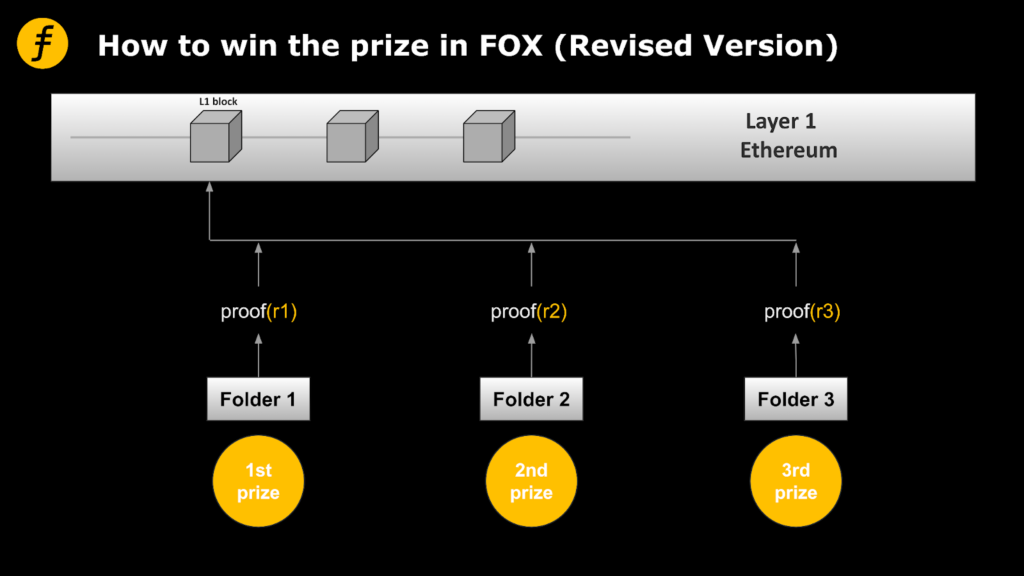
Figure 3: Modified incentive mode
Conclusion
From the point of view of the important role of node charges, this paper introduces the relationship between node charges and how to motivate nodes to participate in system maintenance, and points out that a good incentive mechanism can effectively maintain system security. On this basis, we discuss in detail the incentive mechanism for the Layer2 Folder adopted in FOX, and explain the rationality of this approach, and how to apply the Fiatic-Shamir heuristic to achieve it technically.
Reference Literature
The depth | iteration and competition – the etheric lane of the road to expansion and Layer2, the block chain institute at https://www.theblockbeats.info/news/24443



